mirror of
https://github.com/minio/minio.git
synced 2025-11-21 10:16:03 -05:00
feat: migrate to ROOT_USER/PASSWORD from ACCESS/SECRET_KEY (#11185)
This commit is contained in:
@@ -15,6 +15,8 @@ FROM registry.access.redhat.com/ubi8/ubi-minimal:8.3
|
||||
|
||||
ENV MINIO_ACCESS_KEY_FILE=access_key \
|
||||
MINIO_SECRET_KEY_FILE=secret_key \
|
||||
MINIO_ROOT_USER_FILE=access_key \
|
||||
MINIO_ROOT_PASSWORD_FILE=secret_key \
|
||||
MINIO_KMS_MASTER_KEY_FILE=kms_master_key \
|
||||
MINIO_SSE_MASTER_KEY_FILE=sse_master_key \
|
||||
MINIO_UPDATE_MINISIGN_PUBKEY="RWTx5Zr1tiHQLwG9keckT0c45M3AGeHD6IvimQHpyRywVWGbP1aVSGav"
|
||||
|
||||
@@ -17,6 +17,8 @@ ARG TARGETARCH
|
||||
|
||||
ENV MINIO_ACCESS_KEY_FILE=access_key \
|
||||
MINIO_SECRET_KEY_FILE=secret_key \
|
||||
MINIO_ROOT_USER_FILE=access_key \
|
||||
MINIO_ROOT_PASSWORD_FILE=secret_key \
|
||||
MINIO_KMS_MASTER_KEY_FILE=kms_master_key \
|
||||
MINIO_SSE_MASTER_KEY_FILE=sse_master_key \
|
||||
MINIO_UPDATE_MINISIGN_PUBKEY="RWTx5Zr1tiHQLwG9keckT0c45M3AGeHD6IvimQHpyRywVWGbP1aVSGav"
|
||||
|
||||
@@ -12,6 +12,8 @@ COPY LICENSE /licenses/LICENSE
|
||||
ENV MINIO_UPDATE=off \
|
||||
MINIO_ACCESS_KEY_FILE=access_key \
|
||||
MINIO_SECRET_KEY_FILE=secret_key \
|
||||
MINIO_ROOT_USER_FILE=access_key \
|
||||
MINIO_ROOT_PASSWORD_FILE=secret_key \
|
||||
MINIO_KMS_MASTER_KEY_FILE=kms_master_key \
|
||||
MINIO_SSE_MASTER_KEY_FILE=sse_master_key
|
||||
|
||||
|
||||
@@ -12,6 +12,8 @@ LABEL name="MinIO" \
|
||||
|
||||
ENV MINIO_ACCESS_KEY_FILE=access_key \
|
||||
MINIO_SECRET_KEY_FILE=secret_key \
|
||||
MINIO_ROOT_USER_FILE=access_key \
|
||||
MINIO_ROOT_PASSWORD_FILE=secret_key \
|
||||
MINIO_KMS_MASTER_KEY_FILE=kms_master_key \
|
||||
MINIO_SSE_MASTER_KEY_FILE=sse_master_key \
|
||||
MINIO_UPDATE_MINISIGN_PUBKEY="RWTx5Zr1tiHQLwG9keckT0c45M3AGeHD6IvimQHpyRywVWGbP1aVSGav"
|
||||
|
||||
@@ -9,16 +9,16 @@ MinIO is a High Performance Object Storage released under Apache License v2.0. I
|
||||
### Stable
|
||||
```
|
||||
docker run -p 9000:9000 \
|
||||
-e "MINIO_ACCESS_KEY=AKIAIOSFODNN7EXAMPLE" \
|
||||
-e "MINIO_SECRET_KEY=wJalrXUtnFEMI/K7MDENG/bPxRfiCYEXAMPLEKEY" \
|
||||
-e "MINIO_ROOT_USER=AKIAIOSFODNN7EXAMPLE" \
|
||||
-e "MINIO_ROOT_PASSWORD=wJalrXUtnFEMI/K7MDENG/bPxRfiCYEXAMPLEKEY" \
|
||||
minio/minio server /data
|
||||
```
|
||||
|
||||
### Edge
|
||||
```
|
||||
docker run -p 9000:9000 \
|
||||
-e "MINIO_ACCESS_KEY=AKIAIOSFODNN7EXAMPLE" \
|
||||
-e "MINIO_SECRET_KEY=wJalrXUtnFEMI/K7MDENG/bPxRfiCYEXAMPLEKEY" \
|
||||
-e "MINIO_ROOT_USER=AKIAIOSFODNN7EXAMPLE" \
|
||||
-e "MINIO_ROOT_PASSWORD=wJalrXUtnFEMI/K7MDENG/bPxRfiCYEXAMPLEKEY" \
|
||||
minio/minio:edge server /data
|
||||
```
|
||||
|
||||
|
||||
@@ -8,16 +8,16 @@ MinIO是一个非常轻量的服务,可以很简单的和其他应用的结合
|
||||
### 稳定版
|
||||
```
|
||||
docker run -p 9000:9000 \
|
||||
-e "MINIO_ACCESS_KEY=AKIAIOSFODNN7EXAMPLE" \
|
||||
-e "MINIO_SECRET_KEY=wJalrXUtnFEMI/K7MDENG/bPxRfiCYEXAMPLEKEY" \
|
||||
-e "MINIO_ROOT_USER=AKIAIOSFODNN7EXAMPLE" \
|
||||
-e "MINIO_ROOT_PASSWORD=wJalrXUtnFEMI/K7MDENG/bPxRfiCYEXAMPLEKEY" \
|
||||
minio/minio server /data
|
||||
```
|
||||
|
||||
### 尝鲜版
|
||||
```
|
||||
docker run -p 9000:9000 \
|
||||
-e "MINIO_ACCESS_KEY=AKIAIOSFODNN7EXAMPLE" \
|
||||
-e "MINIO_SECRET_KEY=wJalrXUtnFEMI/K7MDENG/bPxRfiCYEXAMPLEKEY" \
|
||||
-e "MINIO_ROOT_USER=AKIAIOSFODNN7EXAMPLE" \
|
||||
-e "MINIO_ROOT_PASSWORD=wJalrXUtnFEMI/K7MDENG/bPxRfiCYEXAMPLEKEY" \
|
||||
minio/minio:edge server /data
|
||||
```
|
||||
|
||||
|
||||
@@ -1,69 +0,0 @@
|
||||
#!/bin/bash
|
||||
#
|
||||
# MinIO Cloud Storage, (C) 2019 MinIO, Inc.
|
||||
#
|
||||
# Licensed under the Apache License, Version 2.0 (the "License");
|
||||
# you may not use this file except in compliance with the License.
|
||||
# You may obtain a copy of the License at
|
||||
#
|
||||
# http://www.apache.org/licenses/LICENSE-2.0
|
||||
#
|
||||
# Unless required by applicable law or agreed to in writing, software
|
||||
# distributed under the License is distributed on an "AS IS" BASIS,
|
||||
# WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
|
||||
# See the License for the specific language governing permissions and
|
||||
# limitations under the License.
|
||||
#
|
||||
|
||||
set -e
|
||||
set -E
|
||||
set -o pipefail
|
||||
|
||||
function start_minio_server()
|
||||
{
|
||||
MINIO_ACCESS_KEY=minio MINIO_SECRET_KEY=minio123 \
|
||||
minio --quiet --json server /data --address 127.0.0.1:24242 > server.log 2>&1 &
|
||||
server_pid=$!
|
||||
sleep 10
|
||||
|
||||
echo "$server_pid"
|
||||
}
|
||||
|
||||
function start_minio_gateway_s3()
|
||||
{
|
||||
MINIO_ACCESS_KEY=minio MINIO_SECRET_KEY=minio123 \
|
||||
minio --quiet --json gateway s3 http://127.0.0.1:24242 \
|
||||
--address 127.0.0.1:24240 > gateway.log 2>&1 &
|
||||
gw_pid=$!
|
||||
sleep 10
|
||||
|
||||
echo "$gw_pid"
|
||||
}
|
||||
|
||||
function main()
|
||||
{
|
||||
sr_pid="$(start_minio_server)"
|
||||
gw_pid="$(start_minio_gateway_s3)"
|
||||
|
||||
SERVER_ENDPOINT=127.0.0.1:24240 ENABLE_HTTPS=0 ACCESS_KEY=minio \
|
||||
SECRET_KEY=minio123 MINT_MODE="full" /mint/entrypoint.sh \
|
||||
aws-sdk-go aws-sdk-java aws-sdk-php aws-sdk-ruby awscli \
|
||||
healthcheck mc minio-dotnet minio-js \
|
||||
minio-py s3cmd s3select security
|
||||
rv=$?
|
||||
|
||||
kill "$sr_pid"
|
||||
kill "$gw_pid"
|
||||
sleep 3
|
||||
|
||||
if [ "$rv" -ne 0 ]; then
|
||||
echo "=========== Gateway ==========="
|
||||
cat "gateway.log"
|
||||
echo "=========== Server ==========="
|
||||
cat "server.log"
|
||||
fi
|
||||
|
||||
rm -f gateway.log server.log
|
||||
}
|
||||
|
||||
main "$@"
|
||||
@@ -63,8 +63,8 @@ function start_minio_erasure_sets()
|
||||
|
||||
function start_minio_pool_erasure_sets()
|
||||
{
|
||||
export MINIO_ACCESS_KEY=$ACCESS_KEY
|
||||
export MINIO_SECRET_KEY=$SECRET_KEY
|
||||
export MINIO_ROOT_USER=$ACCESS_KEY
|
||||
export MINIO_ROOT_PASSWORD=$SECRET_KEY
|
||||
export MINIO_ENDPOINTS="http://127.0.0.1:9000${WORK_DIR}/pool-disk-sets{1...4} http://127.0.0.1:9001${WORK_DIR}/pool-disk-sets{5...8}"
|
||||
"${MINIO[@]}" server --address ":9000" > "$WORK_DIR/pool-minio-9000.log" 2>&1 &
|
||||
"${MINIO[@]}" server --address ":9001" > "$WORK_DIR/pool-minio-9001.log" 2>&1 &
|
||||
@@ -74,8 +74,8 @@ function start_minio_pool_erasure_sets()
|
||||
|
||||
function start_minio_pool_erasure_sets_ipv6()
|
||||
{
|
||||
export MINIO_ACCESS_KEY=$ACCESS_KEY
|
||||
export MINIO_SECRET_KEY=$SECRET_KEY
|
||||
export MINIO_ROOT_USER=$ACCESS_KEY
|
||||
export MINIO_ROOT_PASSWORD=$SECRET_KEY
|
||||
export MINIO_ENDPOINTS="http://[::1]:9000${WORK_DIR}/pool-disk-sets{1...4} http://[::1]:9001${WORK_DIR}/pool-disk-sets{5...8}"
|
||||
"${MINIO[@]}" server --address="[::1]:9000" > "$WORK_DIR/pool-minio-ipv6-9000.log" 2>&1 &
|
||||
"${MINIO[@]}" server --address="[::1]:9001" > "$WORK_DIR/pool-minio-ipv6-9001.log" 2>&1 &
|
||||
@@ -85,8 +85,8 @@ function start_minio_pool_erasure_sets_ipv6()
|
||||
|
||||
function start_minio_dist_erasure()
|
||||
{
|
||||
export MINIO_ACCESS_KEY=$ACCESS_KEY
|
||||
export MINIO_SECRET_KEY=$SECRET_KEY
|
||||
export MINIO_ROOT_USER=$ACCESS_KEY
|
||||
export MINIO_ROOT_PASSWORD=$SECRET_KEY
|
||||
export MINIO_ENDPOINTS="http://127.0.0.1:9000${WORK_DIR}/dist-disk1 http://127.0.0.1:9001${WORK_DIR}/dist-disk2 http://127.0.0.1:9002${WORK_DIR}/dist-disk3 http://127.0.0.1:9003${WORK_DIR}/dist-disk4"
|
||||
for i in $(seq 0 3); do
|
||||
"${MINIO[@]}" server --address ":900${i}" > "$WORK_DIR/dist-minio-900${i}.log" 2>&1 &
|
||||
|
||||
@@ -29,8 +29,8 @@ MINIO_CONFIG_DIR="$WORK_DIR/.minio"
|
||||
MINIO=( "$PWD/minio" --config-dir "$MINIO_CONFIG_DIR" server )
|
||||
|
||||
function start_minio_3_node() {
|
||||
export MINIO_ACCESS_KEY=minio
|
||||
export MINIO_SECRET_KEY=minio123
|
||||
export MINIO_ROOT_USER=minio
|
||||
export MINIO_ROOT_PASSWORD=minio123
|
||||
export MINIO_ERASURE_SET_DRIVE_COUNT=6
|
||||
|
||||
start_port=$(shuf -i 10000-65000 -n 1)
|
||||
|
||||
@@ -286,6 +286,16 @@ func handleCommonEnvVars() {
|
||||
globalConfigEncrypted = true
|
||||
}
|
||||
|
||||
if env.IsSet(config.EnvRootUser) || env.IsSet(config.EnvRootPassword) {
|
||||
cred, err := auth.CreateCredentials(env.Get(config.EnvRootUser, ""), env.Get(config.EnvRootPassword, ""))
|
||||
if err != nil {
|
||||
logger.Fatal(config.ErrInvalidCredentials(err),
|
||||
"Unable to validate credentials inherited from the shell environment")
|
||||
}
|
||||
globalActiveCred = cred
|
||||
globalConfigEncrypted = true
|
||||
}
|
||||
|
||||
if env.IsSet(config.EnvAccessKeyOld) && env.IsSet(config.EnvSecretKeyOld) {
|
||||
oldCred, err := auth.CreateCredentials(env.Get(config.EnvAccessKeyOld, ""), env.Get(config.EnvSecretKeyOld, ""))
|
||||
if err != nil {
|
||||
@@ -296,6 +306,17 @@ func handleCommonEnvVars() {
|
||||
os.Unsetenv(config.EnvAccessKeyOld)
|
||||
os.Unsetenv(config.EnvSecretKeyOld)
|
||||
}
|
||||
|
||||
if env.IsSet(config.EnvRootUserOld) && env.IsSet(config.EnvRootPasswordOld) {
|
||||
oldCred, err := auth.CreateCredentials(env.Get(config.EnvRootUserOld, ""), env.Get(config.EnvRootPasswordOld, ""))
|
||||
if err != nil {
|
||||
logger.Fatal(config.ErrInvalidCredentials(err),
|
||||
"Unable to validate the old credentials inherited from the shell environment")
|
||||
}
|
||||
globalOldCred = oldCred
|
||||
os.Unsetenv(config.EnvRootUserOld)
|
||||
os.Unsetenv(config.EnvRootPasswordOld)
|
||||
}
|
||||
}
|
||||
|
||||
func logStartupMessage(msg string) {
|
||||
|
||||
@@ -207,7 +207,7 @@ func migrateIAMConfigsEtcdToEncrypted(ctx context.Context, client *etcd.Client)
|
||||
}
|
||||
|
||||
if encrypted && globalActiveCred.IsValid() && globalOldCred.IsValid() {
|
||||
logger.Info("Rotation complete, please make sure to unset MINIO_ACCESS_KEY_OLD and MINIO_SECRET_KEY_OLD envs")
|
||||
logger.Info("Rotation complete, please make sure to unset MINIO_ROOT_USER_OLD and MINIO_ROOT_PASSWORD_OLD envs")
|
||||
}
|
||||
|
||||
return saveKeyEtcd(ctx, client, backendEncryptedFile, backendEncryptedMigrationComplete)
|
||||
@@ -294,7 +294,7 @@ func migrateConfigPrefixToEncrypted(objAPI ObjectLayer, activeCredOld auth.Crede
|
||||
}
|
||||
|
||||
if encrypted && globalActiveCred.IsValid() && activeCredOld.IsValid() {
|
||||
logger.Info("Rotation complete, please make sure to unset MINIO_ACCESS_KEY_OLD and MINIO_SECRET_KEY_OLD envs")
|
||||
logger.Info("Rotation complete, please make sure to unset MINIO_ROOT_USER_OLD and MINIO_ROOT_PASSWORD_OLD envs")
|
||||
}
|
||||
|
||||
return saveConfig(GlobalContext, objAPI, backendEncryptedFile, backendEncryptedMigrationComplete)
|
||||
|
||||
@@ -23,17 +23,21 @@ const (
|
||||
|
||||
// Top level common ENVs
|
||||
const (
|
||||
EnvAccessKey = "MINIO_ACCESS_KEY"
|
||||
EnvSecretKey = "MINIO_SECRET_KEY"
|
||||
EnvAccessKeyOld = "MINIO_ACCESS_KEY_OLD"
|
||||
EnvSecretKeyOld = "MINIO_SECRET_KEY_OLD"
|
||||
EnvBrowser = "MINIO_BROWSER"
|
||||
EnvDomain = "MINIO_DOMAIN"
|
||||
EnvRegionName = "MINIO_REGION_NAME"
|
||||
EnvPublicIPs = "MINIO_PUBLIC_IPS"
|
||||
EnvFSOSync = "MINIO_FS_OSYNC"
|
||||
EnvArgs = "MINIO_ARGS"
|
||||
EnvDNSWebhook = "MINIO_DNS_WEBHOOK_ENDPOINT"
|
||||
EnvAccessKey = "MINIO_ACCESS_KEY"
|
||||
EnvSecretKey = "MINIO_SECRET_KEY"
|
||||
EnvRootUser = "MINIO_ROOT_USER"
|
||||
EnvRootPassword = "MINIO_ROOT_PASSWORD"
|
||||
EnvAccessKeyOld = "MINIO_ACCESS_KEY_OLD"
|
||||
EnvSecretKeyOld = "MINIO_SECRET_KEY_OLD"
|
||||
EnvRootUserOld = "MINIO_ROOT_USER_OLD"
|
||||
EnvRootPasswordOld = "MINIO_ROOT_PASSWORD_OLD"
|
||||
EnvBrowser = "MINIO_BROWSER"
|
||||
EnvDomain = "MINIO_DOMAIN"
|
||||
EnvRegionName = "MINIO_REGION_NAME"
|
||||
EnvPublicIPs = "MINIO_PUBLIC_IPS"
|
||||
EnvFSOSync = "MINIO_FS_OSYNC"
|
||||
EnvArgs = "MINIO_ARGS"
|
||||
EnvDNSWebhook = "MINIO_DNS_WEBHOOK_ENDPOINT"
|
||||
|
||||
EnvUpdate = "MINIO_UPDATE"
|
||||
|
||||
|
||||
@@ -116,19 +116,19 @@ var (
|
||||
ErrInvalidRotatingCredentialsBackendEncrypted = newErrFn(
|
||||
"Invalid rotating credentials",
|
||||
"Please set correct rotating credentials in the environment for decryption",
|
||||
`Detected encrypted config backend, correct old access and secret keys should be specified via environment variables MINIO_ACCESS_KEY_OLD and MINIO_SECRET_KEY_OLD to be able to re-encrypt the MinIO config, user IAM and policies with new credentials`,
|
||||
`Detected encrypted config backend, correct old access and secret keys should be specified via environment variables MINIO_ROOT_USER_OLD and MINIO_ROOT_PASSWORD_OLD to be able to re-encrypt the MinIO config, user IAM and policies with new credentials`,
|
||||
)
|
||||
|
||||
ErrInvalidCredentialsBackendEncrypted = newErrFn(
|
||||
"Invalid credentials",
|
||||
"Please set correct credentials in the environment for decryption",
|
||||
`Detected encrypted config backend, correct access and secret keys should be specified via environment variables MINIO_ACCESS_KEY and MINIO_SECRET_KEY to be able to decrypt the MinIO config, user IAM and policies`,
|
||||
`Detected encrypted config backend, correct access and secret keys should be specified via environment variables MINIO_ROOT_USER and MINIO_ROOT_PASSWORD to be able to decrypt the MinIO config, user IAM and policies`,
|
||||
)
|
||||
|
||||
ErrMissingCredentialsBackendEncrypted = newErrFn(
|
||||
"Credentials missing",
|
||||
"Please set your credentials in the environment",
|
||||
`Detected encrypted config backend, access and secret keys should be specified via environment variables MINIO_ACCESS_KEY and MINIO_SECRET_KEY to be able to decrypt the MinIO config, user IAM and policies`,
|
||||
`Detected encrypted config backend, access and secret keys should be specified via environment variables MINIO_ROOT_USER and MINIO_ROOT_PASSWORD to be able to decrypt the MinIO config, user IAM and policies`,
|
||||
)
|
||||
|
||||
ErrInvalidCredentials = newErrFn(
|
||||
@@ -140,13 +140,13 @@ var (
|
||||
ErrEnvCredentialsMissingGateway = newErrFn(
|
||||
"Credentials missing",
|
||||
"Please set your credentials in the environment",
|
||||
`In Gateway mode, access and secret keys should be specified via environment variables MINIO_ACCESS_KEY and MINIO_SECRET_KEY respectively`,
|
||||
`In Gateway mode, access and secret keys should be specified via environment variables MINIO_ROOT_USER and MINIO_ROOT_PASSWORD respectively`,
|
||||
)
|
||||
|
||||
ErrEnvCredentialsMissingDistributed = newErrFn(
|
||||
"Credentials missing",
|
||||
"Please set your credentials in the environment",
|
||||
`In distributed server mode, access and secret keys should be specified via environment variables MINIO_ACCESS_KEY and MINIO_SECRET_KEY respectively`,
|
||||
`In distributed server mode, access and secret keys should be specified via environment variables MINIO_ROOT_USER and MINIO_ROOT_PASSWORD respectively`,
|
||||
)
|
||||
|
||||
ErrInvalidErasureEndpoints = newErrFn(
|
||||
|
||||
@@ -60,8 +60,8 @@ func printGatewayCommonMsg(apiEndpoints []string) {
|
||||
// Colorize the message and print.
|
||||
logStartupMessage(color.Blue("Endpoint: ") + color.Bold(fmt.Sprintf(getFormatStr(len(apiEndpointStr), 1), apiEndpointStr)))
|
||||
if color.IsTerminal() && !globalCLIContext.Anonymous {
|
||||
logStartupMessage(color.Blue("AccessKey: ") + color.Bold(fmt.Sprintf("%s ", cred.AccessKey)))
|
||||
logStartupMessage(color.Blue("SecretKey: ") + color.Bold(fmt.Sprintf("%s ", cred.SecretKey)))
|
||||
logStartupMessage(color.Blue("RootUser: ") + color.Bold(fmt.Sprintf("%s ", cred.AccessKey)))
|
||||
logStartupMessage(color.Blue("RootPassword: ") + color.Bold(fmt.Sprintf("%s ", cred.SecretKey)))
|
||||
}
|
||||
printEventNotifiers()
|
||||
|
||||
|
||||
@@ -92,14 +92,14 @@ ENDPOINT:
|
||||
|
||||
EXAMPLES:
|
||||
1. Start minio gateway server for Azure Blob Storage backend on custom endpoint.
|
||||
{{.Prompt}} {{.EnvVarSetCommand}} MINIO_ACCESS_KEY{{.AssignmentOperator}}azureaccountname
|
||||
{{.Prompt}} {{.EnvVarSetCommand}} MINIO_SECRET_KEY{{.AssignmentOperator}}azureaccountkey
|
||||
{{.Prompt}} {{.EnvVarSetCommand}} MINIO_ROOT_USER{{.AssignmentOperator}}azureaccountname
|
||||
{{.Prompt}} {{.EnvVarSetCommand}} MINIO_ROOT_PASSWORD{{.AssignmentOperator}}azureaccountkey
|
||||
{{.Prompt}} {{.EnvVarSetCommand}} MINIO_AZURE_CHUNK_SIZE_MB {{.AssignmentOperator}}0.25
|
||||
{{.Prompt}} {{.HelpName}} https://azureaccountname.blob.custom.azure.endpoint
|
||||
|
||||
2. Start minio gateway server for Azure Blob Storage backend with edge caching enabled.
|
||||
{{.Prompt}} {{.EnvVarSetCommand}} MINIO_ACCESS_KEY{{.AssignmentOperator}}azureaccountname
|
||||
{{.Prompt}} {{.EnvVarSetCommand}} MINIO_SECRET_KEY{{.AssignmentOperator}}azureaccountkey
|
||||
{{.Prompt}} {{.EnvVarSetCommand}} MINIO_ROOT_USER{{.AssignmentOperator}}azureaccountname
|
||||
{{.Prompt}} {{.EnvVarSetCommand}} MINIO_ROOT_PASSWORD{{.AssignmentOperator}}azureaccountkey
|
||||
{{.Prompt}} {{.EnvVarSetCommand}} MINIO_CACHE_DRIVES{{.AssignmentOperator}}"/mnt/drive1,/mnt/drive2,/mnt/drive3,/mnt/drive4"
|
||||
{{.Prompt}} {{.EnvVarSetCommand}} MINIO_CACHE_EXCLUDE{{.AssignmentOperator}}"bucket1/*,*.png"
|
||||
{{.Prompt}} {{.EnvVarSetCommand}} MINIO_CACHE_QUOTA{{.AssignmentOperator}}90
|
||||
|
||||
@@ -112,14 +112,14 @@ GOOGLE_APPLICATION_CREDENTIALS:
|
||||
EXAMPLES:
|
||||
1. Start minio gateway server for GCS backend
|
||||
{{.Prompt}} {{.EnvVarSetCommand}} GOOGLE_APPLICATION_CREDENTIALS{{.AssignmentOperator}}/path/to/credentials.json
|
||||
{{.Prompt}} {{.EnvVarSetCommand}} MINIO_ACCESS_KEY{{.AssignmentOperator}}accesskey
|
||||
{{.Prompt}} {{.EnvVarSetCommand}} MINIO_SECRET_KEY{{.AssignmentOperator}}secretkey
|
||||
{{.Prompt}} {{.EnvVarSetCommand}} MINIO_ROOT_USER{{.AssignmentOperator}}accesskey
|
||||
{{.Prompt}} {{.EnvVarSetCommand}} MINIO_ROOT_PASSWORD{{.AssignmentOperator}}secretkey
|
||||
{{.Prompt}} {{.HelpName}} mygcsprojectid
|
||||
|
||||
2. Start minio gateway server for GCS backend with edge caching enabled
|
||||
{{.Prompt}} {{.EnvVarSetCommand}} GOOGLE_APPLICATION_CREDENTIALS{{.AssignmentOperator}}/path/to/credentials.json
|
||||
{{.Prompt}} {{.EnvVarSetCommand}} MINIO_ACCESS_KEY{{.AssignmentOperator}}accesskey
|
||||
{{.Prompt}} {{.EnvVarSetCommand}} MINIO_SECRET_KEY{{.AssignmentOperator}}secretkey
|
||||
{{.Prompt}} {{.EnvVarSetCommand}} MINIO_ROOT_USER{{.AssignmentOperator}}accesskey
|
||||
{{.Prompt}} {{.EnvVarSetCommand}} MINIO_ROOT_PASSWORD{{.AssignmentOperator}}secretkey
|
||||
{{.Prompt}} {{.EnvVarSetCommand}} MINIO_CACHE_DRIVES{{.AssignmentOperator}}"/mnt/drive1,/mnt/drive2,/mnt/drive3,/mnt/drive4"
|
||||
{{.Prompt}} {{.EnvVarSetCommand}} MINIO_CACHE_EXCLUDE{{.AssignmentOperator}}"bucket1/*;*.png"
|
||||
{{.Prompt}} {{.EnvVarSetCommand}} MINIO_CACHE_AFTER{{.AssignmentOperator}}3
|
||||
|
||||
@@ -65,13 +65,13 @@ HDFS-NAMENODE:
|
||||
|
||||
EXAMPLES:
|
||||
1. Start minio gateway server for HDFS backend
|
||||
{{.Prompt}} {{.EnvVarSetCommand}} MINIO_ACCESS_KEY{{.AssignmentOperator}}accesskey
|
||||
{{.Prompt}} {{.EnvVarSetCommand}} MINIO_SECRET_KEY{{.AssignmentOperator}}secretkey
|
||||
{{.Prompt}} {{.EnvVarSetCommand}} MINIO_ROOT_USER{{.AssignmentOperator}}accesskey
|
||||
{{.Prompt}} {{.EnvVarSetCommand}} MINIO_ROOT_PASSWORD{{.AssignmentOperator}}secretkey
|
||||
{{.Prompt}} {{.HelpName}} hdfs://namenode:8200
|
||||
|
||||
2. Start minio gateway server for HDFS with edge caching enabled
|
||||
{{.Prompt}} {{.EnvVarSetCommand}} MINIO_ACCESS_KEY{{.AssignmentOperator}}accesskey
|
||||
{{.Prompt}} {{.EnvVarSetCommand}} MINIO_SECRET_KEY{{.AssignmentOperator}}secretkey
|
||||
{{.Prompt}} {{.EnvVarSetCommand}} MINIO_ROOT_USER{{.AssignmentOperator}}accesskey
|
||||
{{.Prompt}} {{.EnvVarSetCommand}} MINIO_ROOT_PASSWORD{{.AssignmentOperator}}secretkey
|
||||
{{.Prompt}} {{.EnvVarSetCommand}} MINIO_CACHE_DRIVES{{.AssignmentOperator}}"/mnt/drive1,/mnt/drive2,/mnt/drive3,/mnt/drive4"
|
||||
{{.Prompt}} {{.EnvVarSetCommand}} MINIO_CACHE_EXCLUDE{{.AssignmentOperator}}"bucket1/*,*.png"
|
||||
{{.Prompt}} {{.EnvVarSetCommand}} MINIO_CACHE_QUOTA{{.AssignmentOperator}}90
|
||||
|
||||
@@ -39,13 +39,13 @@ PATH:
|
||||
|
||||
EXAMPLES:
|
||||
1. Start minio gateway server for NAS backend
|
||||
{{.Prompt}} {{.EnvVarSetCommand}} MINIO_ACCESS_KEY{{.AssignmentOperator}}accesskey
|
||||
{{.Prompt}} {{.EnvVarSetCommand}} MINIO_SECRET_KEY{{.AssignmentOperator}}secretkey
|
||||
{{.Prompt}} {{.EnvVarSetCommand}} MINIO_ROOT_USER{{.AssignmentOperator}}accesskey
|
||||
{{.Prompt}} {{.EnvVarSetCommand}} MINIO_ROOT_PASSWORD{{.AssignmentOperator}}secretkey
|
||||
{{.Prompt}} {{.HelpName}} /shared/nasvol
|
||||
|
||||
2. Start minio gateway server for NAS with edge caching enabled
|
||||
{{.Prompt}} {{.EnvVarSetCommand}} MINIO_ACCESS_KEY{{.AssignmentOperator}}accesskey
|
||||
{{.Prompt}} {{.EnvVarSetCommand}} MINIO_SECRET_KEY{{.AssignmentOperator}}secretkey
|
||||
{{.Prompt}} {{.EnvVarSetCommand}} MINIO_ROOT_USER{{.AssignmentOperator}}accesskey
|
||||
{{.Prompt}} {{.EnvVarSetCommand}} MINIO_ROOT_PASSWORD{{.AssignmentOperator}}secretkey
|
||||
{{.Prompt}} {{.EnvVarSetCommand}} MINIO_CACHE_DRIVES{{.AssignmentOperator}}"/mnt/drive1,/mnt/drive2,/mnt/drive3,/mnt/drive4"
|
||||
{{.Prompt}} {{.EnvVarSetCommand}} MINIO_CACHE_EXCLUDE{{.AssignmentOperator}}"bucket1/*,*.png"
|
||||
{{.Prompt}} {{.EnvVarSetCommand}} MINIO_CACHE_QUOTA{{.AssignmentOperator}}90
|
||||
|
||||
@@ -55,13 +55,13 @@ ENDPOINT:
|
||||
|
||||
EXAMPLES:
|
||||
1. Start minio gateway server for AWS S3 backend
|
||||
{{.Prompt}} {{.EnvVarSetCommand}} MINIO_ACCESS_KEY{{.AssignmentOperator}}accesskey
|
||||
{{.Prompt}} {{.EnvVarSetCommand}} MINIO_SECRET_KEY{{.AssignmentOperator}}secretkey
|
||||
{{.Prompt}} {{.EnvVarSetCommand}} MINIO_ROOT_USER{{.AssignmentOperator}}accesskey
|
||||
{{.Prompt}} {{.EnvVarSetCommand}} MINIO_ROOT_PASSWORD{{.AssignmentOperator}}secretkey
|
||||
{{.Prompt}} {{.HelpName}}
|
||||
|
||||
2. Start minio gateway server for AWS S3 backend with edge caching enabled
|
||||
{{.Prompt}} {{.EnvVarSetCommand}} MINIO_ACCESS_KEY{{.AssignmentOperator}}accesskey
|
||||
{{.Prompt}} {{.EnvVarSetCommand}} MINIO_SECRET_KEY{{.AssignmentOperator}}secretkey
|
||||
{{.Prompt}} {{.EnvVarSetCommand}} MINIO_ROOT_USER{{.AssignmentOperator}}accesskey
|
||||
{{.Prompt}} {{.EnvVarSetCommand}} MINIO_ROOT_PASSWORD{{.AssignmentOperator}}secretkey
|
||||
{{.Prompt}} {{.EnvVarSetCommand}} MINIO_CACHE_DRIVES{{.AssignmentOperator}}"/mnt/drive1,/mnt/drive2,/mnt/drive3,/mnt/drive4"
|
||||
{{.Prompt}} {{.EnvVarSetCommand}} MINIO_CACHE_EXCLUDE{{.AssignmentOperator}}"bucket1/*,*.png"
|
||||
{{.Prompt}} {{.EnvVarSetCommand}} MINIO_CACHE_QUOTA{{.AssignmentOperator}}90
|
||||
@@ -136,7 +136,7 @@ func randString(n int, src rand.Source, prefix string) string {
|
||||
// Chains all credential types, in the following order:
|
||||
// - AWS env vars (i.e. AWS_ACCESS_KEY_ID)
|
||||
// - AWS creds file (i.e. AWS_SHARED_CREDENTIALS_FILE or ~/.aws/credentials)
|
||||
// - Static credentials provided by user (i.e. MINIO_ACCESS_KEY)
|
||||
// - Static credentials provided by user (i.e. MINIO_ROOT_USER)
|
||||
var defaultProviders = []credentials.Provider{
|
||||
&credentials.EnvAWS{},
|
||||
&credentials.FileAWSCredentials{},
|
||||
|
||||
@@ -83,13 +83,13 @@ EXAMPLES:
|
||||
{{.Prompt}} {{.HelpName}} /mnt/data{1...64}
|
||||
|
||||
3. Start distributed minio server on an 32 node setup with 32 drives each, run following command on all the nodes
|
||||
{{.Prompt}} {{.EnvVarSetCommand}} MINIO_ACCESS_KEY{{.AssignmentOperator}}minio
|
||||
{{.Prompt}} {{.EnvVarSetCommand}} MINIO_SECRET_KEY{{.AssignmentOperator}}miniostorage
|
||||
{{.Prompt}} {{.EnvVarSetCommand}} MINIO_ROOT_USER{{.AssignmentOperator}}minio
|
||||
{{.Prompt}} {{.EnvVarSetCommand}} MINIO_ROOT_PASSWORD{{.AssignmentOperator}}miniostorage
|
||||
{{.Prompt}} {{.HelpName}} http://node{1...32}.example.com/mnt/export{1...32}
|
||||
|
||||
4. Start distributed minio server in an expanded setup, run the following command on all the nodes
|
||||
{{.Prompt}} {{.EnvVarSetCommand}} MINIO_ACCESS_KEY{{.AssignmentOperator}}minio
|
||||
{{.Prompt}} {{.EnvVarSetCommand}} MINIO_SECRET_KEY{{.AssignmentOperator}}miniostorage
|
||||
{{.Prompt}} {{.EnvVarSetCommand}} MINIO_ROOT_USER{{.AssignmentOperator}}minio
|
||||
{{.Prompt}} {{.EnvVarSetCommand}} MINIO_ROOT_PASSWORD{{.AssignmentOperator}}miniostorage
|
||||
{{.Prompt}} {{.HelpName}} http://node{1...16}.example.com/mnt/export{1...32} \
|
||||
http://node{17...64}.example.com/mnt/export{1...64}
|
||||
`,
|
||||
@@ -511,7 +511,7 @@ func serverMain(ctx *cli.Context) {
|
||||
printStartupMessage(getAPIEndpoints(), err)
|
||||
|
||||
if globalActiveCred.Equal(auth.DefaultCredentials) {
|
||||
msg := fmt.Sprintf("Detected default credentials '%s', please change the credentials immediately using 'MINIO_ACCESS_KEY' and 'MINIO_SECRET_KEY'", globalActiveCred)
|
||||
msg := fmt.Sprintf("Detected default credentials '%s', please change the credentials immediately using 'MINIO_ROOT_USER' and 'MINIO_ROOT_PASSWORD'", globalActiveCred)
|
||||
logger.StartupMessage(color.RedBold(msg))
|
||||
}
|
||||
|
||||
|
||||
@@ -137,8 +137,8 @@ func printServerCommonMsg(apiEndpoints []string) {
|
||||
// Colorize the message and print.
|
||||
logStartupMessage(color.Blue("Endpoint: ") + color.Bold(fmt.Sprintf(getFormatStr(len(apiEndpointStr), 1), apiEndpointStr)))
|
||||
if color.IsTerminal() && !globalCLIContext.Anonymous {
|
||||
logStartupMessage(color.Blue("AccessKey: ") + color.Bold(fmt.Sprintf("%s ", cred.AccessKey)))
|
||||
logStartupMessage(color.Blue("SecretKey: ") + color.Bold(fmt.Sprintf("%s ", cred.SecretKey)))
|
||||
logStartupMessage(color.Blue("RootUser: ") + color.Bold(fmt.Sprintf("%s ", cred.AccessKey)))
|
||||
logStartupMessage(color.Blue("RootPassword: ") + color.Bold(fmt.Sprintf("%s ", cred.SecretKey)))
|
||||
if region != "" {
|
||||
logStartupMessage(color.Blue("Region: ") + color.Bold(fmt.Sprintf(getFormatStr(len(region), 3), region)))
|
||||
}
|
||||
|
||||
@@ -23,7 +23,7 @@ if [ "${1}" != "minio" ]; then
|
||||
fi
|
||||
|
||||
## Look for docker secrets at given absolute path or in default documented location.
|
||||
docker_secrets_env() {
|
||||
docker_secrets_env_old() {
|
||||
if [ -f "$MINIO_ACCESS_KEY_FILE" ]; then
|
||||
ACCESS_KEY_FILE="$MINIO_ACCESS_KEY_FILE"
|
||||
else
|
||||
@@ -47,6 +47,30 @@ docker_secrets_env() {
|
||||
fi
|
||||
}
|
||||
|
||||
docker_secrets_env() {
|
||||
if [ -f "$MINIO_ROOT_USER_FILE" ]; then
|
||||
ROOT_USER_FILE="$MINIO_ROOT_USER_FILE"
|
||||
else
|
||||
ROOT_USER_FILE="/run/secrets/$MINIO_ROOT_USER_FILE"
|
||||
fi
|
||||
if [ -f "$MINIO_ROOT_PASSWORD_FILE" ]; then
|
||||
SECRET_KEY_FILE="$MINIO_ROOT_PASSWORD_FILE"
|
||||
else
|
||||
SECRET_KEY_FILE="/run/secrets/$MINIO_ROOT_PASSWORD_FILE"
|
||||
fi
|
||||
|
||||
if [ -f "$ROOT_USER_FILE" ] && [ -f "$SECRET_KEY_FILE" ]; then
|
||||
if [ -f "$ROOT_USER_FILE" ]; then
|
||||
MINIO_ROOT_USER="$(cat "$ROOT_USER_FILE")"
|
||||
export MINIO_ROOT_USER
|
||||
fi
|
||||
if [ -f "$SECRET_KEY_FILE" ]; then
|
||||
MINIO_ROOT_PASSWORD="$(cat "$SECRET_KEY_FILE")"
|
||||
export MINIO_ROOT_PASSWORD
|
||||
fi
|
||||
fi
|
||||
}
|
||||
|
||||
## Set KMS_MASTER_KEY from docker secrets if provided
|
||||
docker_kms_encryption_env() {
|
||||
if [ -f "$MINIO_KMS_MASTER_KEY_FILE" ]; then
|
||||
@@ -88,6 +112,9 @@ docker_switch_user() {
|
||||
fi
|
||||
}
|
||||
|
||||
## Set access env from secrets if necessary.
|
||||
docker_secrets_env_old
|
||||
|
||||
## Set access env from secrets if necessary.
|
||||
docker_secrets_env
|
||||
|
||||
|
||||
@@ -32,11 +32,11 @@ $ mc tree --files ~/.minio
|
||||
You can provide a custom certs directory using `--certs-dir` command line option.
|
||||
|
||||
#### Credentials
|
||||
On MinIO admin credentials or root credentials are only allowed to be changed using ENVs namely `MINIO_ACCESS_KEY` and `MINIO_SECRET_KEY`. Using the combination of these two values MinIO encrypts the config stored at the backend.
|
||||
On MinIO admin credentials or root credentials are only allowed to be changed using ENVs namely `MINIO_ROOT_USER` and `MINIO_ROOT_PASSWORD`. Using the combination of these two values MinIO encrypts the config stored at the backend.
|
||||
|
||||
```sh
|
||||
export MINIO_ACCESS_KEY=minio
|
||||
export MINIO_SECRET_KEY=minio13
|
||||
export MINIO_ROOT_USER=minio
|
||||
export MINIO_ROOT_PASSWORD=minio13
|
||||
minio server /data
|
||||
```
|
||||
|
||||
@@ -47,16 +47,16 @@ Additionally if you wish to change the admin credentials, then MinIO will automa
|
||||
> Old ENVs are never remembered in memory and are destroyed right after they are used to migrate your existing content with new credentials. You are safe to remove them after the server as successfully started, by restarting the services once again.
|
||||
|
||||
```sh
|
||||
export MINIO_ACCESS_KEY=newminio
|
||||
export MINIO_SECRET_KEY=newminio123
|
||||
export MINIO_ACCESS_KEY_OLD=minio
|
||||
export MINIO_SECRET_KEY_OLD=minio123
|
||||
export MINIO_ROOT_USER=newminio
|
||||
export MINIO_ROOT_PASSWORD=newminio123
|
||||
export MINIO_ROOT_USER_OLD=minio
|
||||
export MINIO_ROOT_PASSWORD_OLD=minio123
|
||||
minio server /data
|
||||
```
|
||||
|
||||
Once the migration is complete, server will automatically unset the `MINIO_ACCESS_KEY_OLD` and `MINIO_SECRET_KEY_OLD` with in the process namespace.
|
||||
Once the migration is complete, server will automatically unset the `MINIO_ROOT_USER_OLD` and `MINIO_ROOT_PASSWORD_OLD` with in the process namespace.
|
||||
|
||||
> **NOTE: Make sure to remove `MINIO_ACCESS_KEY_OLD` and `MINIO_SECRET_KEY_OLD` in scripts or service files before next service restarts of the server to avoid double encryption of your existing contents.**
|
||||
> **NOTE: Make sure to remove `MINIO_ROOT_USER_OLD` and `MINIO_ROOT_PASSWORD_OLD` in scripts or service files before next service restarts of the server to avoid double encryption of your existing contents.**
|
||||
|
||||
#### Region
|
||||
```
|
||||
|
||||
@@ -37,14 +37,21 @@ minio gateway <name> -h
|
||||
### Stable
|
||||
Cache drives need to have `strictatime` or `relatime` enabled for disk caching feature. In this example, mount the xfs file system on /mnt/cache with `strictatime` or `relatime` enabled.
|
||||
|
||||
```
|
||||
```sh
|
||||
truncate -s 4G /tmp/data
|
||||
mkfs.xfs /tmp/data # build xfs filesystem on /tmp/data
|
||||
sudo mkdir /mnt/cache # create mount dir
|
||||
sudo mount -o relatime /tmp/data /mnt/cache # mount xfs on /mnt/cache with atime.
|
||||
docker pull minio/minio
|
||||
docker run --net=host -e MINIO_ACCESS_KEY={s3-access-key} -e MINIO_SECRET_KEY={s3-secret-key} -e MINIO_CACHE_DRIVES=/cache -e MINIO_CACHE_QUOTA=99 -e MINIO_CACHE_AFTER=0 -e MINIO_CACHE_WATERMARK_LOW=90 -e MINIO_CACHE_WATERMARK_HIGH=95 -v /mnt/cache:/cache minio/minio:latest gateway s3
|
||||
|
||||
mkfs.xfs /tmp/data # build xfs filesystem on /tmp/data
|
||||
|
||||
sudo mkdir /mnt/cache # create mount dir
|
||||
|
||||
sudo mount -o relatime /tmp/data /mnt/cache # mount xfs on /mnt/cache with atime.
|
||||
|
||||
docker pull minio/minio
|
||||
|
||||
docker run --net=host -e MINIO_ROOT_USER={s3-access-key} -e MINIO_ROOT_PASSWORD={s3-secret-key} \
|
||||
-e MINIO_CACHE_DRIVES=/cache -e MINIO_CACHE_QUOTA=99 -e MINIO_CACHE_AFTER=0 \
|
||||
-e MINIO_CACHE_WATERMARK_LOW=90 -e MINIO_CACHE_WATERMARK_HIGH=95 \
|
||||
-v /mnt/cache:/cache minio/minio:latest gateway s3
|
||||
```
|
||||
|
||||
## Assumptions
|
||||
|
||||
@@ -36,7 +36,7 @@ To start a distributed MinIO instance, you just need to pass drive locations as
|
||||
|
||||
__NOTE:__
|
||||
|
||||
- All the nodes running distributed MinIO need to have same access key and secret key for the nodes to connect. To achieve this, it is __recommended__ to export access key and secret key as environment variables, `MINIO_ACCESS_KEY` and `MINIO_SECRET_KEY`, on all the nodes before executing MinIO server command.
|
||||
- All the nodes running distributed MinIO need to have same access key and secret key for the nodes to connect. To achieve this, it is __recommended__ to export access key and secret key as environment variables, `MINIO_ROOT_USER` and `MINIO_ROOT_PASSWORD`, on all the nodes before executing MinIO server command.
|
||||
- __MinIO creates erasure-coding sets of *4* to *16* drives per set. The number of drives you provide in total must be a multiple of one of those numbers.__
|
||||
- __MinIO chooses the largest EC set size which divides into the total number of drives or total number of nodes given - making sure to keep the uniform distribution i.e each node participates equal number of drives per set.
|
||||
- __Each object is written to a single EC set, and therefore is spread over no more than 16 drives.__
|
||||
@@ -54,8 +54,8 @@ Example 1: Start distributed MinIO instance on n nodes with m drives each mounte
|
||||
#### GNU/Linux and macOS
|
||||
|
||||
```sh
|
||||
export MINIO_ACCESS_KEY=<ACCESS_KEY>
|
||||
export MINIO_SECRET_KEY=<SECRET_KEY>
|
||||
export MINIO_ROOT_USER=<ACCESS_KEY>
|
||||
export MINIO_ROOT_PASSWORD=<SECRET_KEY>
|
||||
minio server http://host{1...n}/export{1...m}
|
||||
```
|
||||
|
||||
@@ -67,8 +67,8 @@ minio server http://host{1...n}/export{1...m}
|
||||
MinIO supports expanding distributed erasure coded clusters by specifying new set of clusters on the command-line as shown below:
|
||||
|
||||
```sh
|
||||
export MINIO_ACCESS_KEY=<ACCESS_KEY>
|
||||
export MINIO_SECRET_KEY=<SECRET_KEY>
|
||||
export MINIO_ROOT_USER=<ACCESS_KEY>
|
||||
export MINIO_ROOT_PASSWORD=<SECRET_KEY>
|
||||
minio server http://host{1...n}/export{1...m} http://host{o...z}/export{1...m}
|
||||
```
|
||||
|
||||
|
||||
@@ -8,8 +8,8 @@ MinIO needs a persistent volume to store configuration and application data. How
|
||||
|
||||
```sh
|
||||
docker run -p 9000:9000 \
|
||||
-e "MINIO_ACCESS_KEY=AKIAIOSFODNN7EXAMPLE" \
|
||||
-e "MINIO_SECRET_KEY=wJalrXUtnFEMI/K7MDENG/bPxRfiCYEXAMPLEKEY" \
|
||||
-e "MINIO_ROOT_USER=AKIAIOSFODNN7EXAMPLE" \
|
||||
-e "MINIO_ROOT_PASSWORD=wJalrXUtnFEMI/K7MDENG/bPxRfiCYEXAMPLEKEY" \
|
||||
minio/minio server /data
|
||||
```
|
||||
|
||||
@@ -20,8 +20,8 @@ To create a MinIO container with persistent storage, you need to map local persi
|
||||
docker run -p 9000:9000 \
|
||||
--name minio1 \
|
||||
-v /mnt/data:/data \
|
||||
-e "MINIO_ACCESS_KEY=AKIAIOSFODNN7EXAMPLE" \
|
||||
-e "MINIO_SECRET_KEY=wJalrXUtnFEMI/K7MDENG/bPxRfiCYEXAMPLEKEY" \
|
||||
-e "MINIO_ROOT_USER=AKIAIOSFODNN7EXAMPLE" \
|
||||
-e "MINIO_ROOT_PASSWORD=wJalrXUtnFEMI/K7MDENG/bPxRfiCYEXAMPLEKEY" \
|
||||
minio/minio server /data
|
||||
```
|
||||
|
||||
@@ -30,8 +30,8 @@ docker run -p 9000:9000 \
|
||||
docker run -p 9000:9000 \
|
||||
--name minio1 \
|
||||
-v D:\data:/data \
|
||||
-e "MINIO_ACCESS_KEY=AKIAIOSFODNN7EXAMPLE" \
|
||||
-e "MINIO_SECRET_KEY=wJalrXUtnFEMI/K7MDENG/bPxRfiCYEXAMPLEKEY" \
|
||||
-e "MINIO_ROOT_USER=AKIAIOSFODNN7EXAMPLE" \
|
||||
-e "MINIO_ROOT_PASSWORD=wJalrXUtnFEMI/K7MDENG/bPxRfiCYEXAMPLEKEY" \
|
||||
minio/minio server /data
|
||||
```
|
||||
|
||||
@@ -48,8 +48,8 @@ To override MinIO's auto-generated keys, you may pass secret and access keys exp
|
||||
#### GNU/Linux and macOS
|
||||
```sh
|
||||
docker run -p 9000:9000 --name minio1 \
|
||||
-e "MINIO_ACCESS_KEY=AKIAIOSFODNN7EXAMPLE" \
|
||||
-e "MINIO_SECRET_KEY=wJalrXUtnFEMI/K7MDENG/bPxRfiCYEXAMPLEKEY" \
|
||||
-e "MINIO_ROOT_USER=AKIAIOSFODNN7EXAMPLE" \
|
||||
-e "MINIO_ROOT_PASSWORD=wJalrXUtnFEMI/K7MDENG/bPxRfiCYEXAMPLEKEY" \
|
||||
-v /mnt/data:/data \
|
||||
minio/minio server /data
|
||||
```
|
||||
@@ -57,8 +57,8 @@ docker run -p 9000:9000 --name minio1 \
|
||||
#### Windows
|
||||
```powershell
|
||||
docker run -p 9000:9000 --name minio1 \
|
||||
-e "MINIO_ACCESS_KEY=AKIAIOSFODNN7EXAMPLE" \
|
||||
-e "MINIO_SECRET_KEY=wJalrXUtnFEMI/K7MDENG/bPxRfiCYEXAMPLEKEY" \
|
||||
-e "MINIO_ROOT_USER=AKIAIOSFODNN7EXAMPLE" \
|
||||
-e "MINIO_ROOT_PASSWORD=wJalrXUtnFEMI/K7MDENG/bPxRfiCYEXAMPLEKEY" \
|
||||
-v D:\data:/data \
|
||||
minio/minio server /data
|
||||
```
|
||||
@@ -75,8 +75,8 @@ mkdir -p ${HOME}/data
|
||||
docker run -p 9000:9000 \
|
||||
--user $(id -u):$(id -g) \
|
||||
--name minio1 \
|
||||
-e "MINIO_ACCESS_KEY=AKIAIOSFODNN7EXAMPLE" \
|
||||
-e "MINIO_SECRET_KEY=wJalrXUtnFEMIK7MDENGbPxRfiCYEXAMPLEKEY" \
|
||||
-e "MINIO_ROOT_USER=AKIAIOSFODNN7EXAMPLE" \
|
||||
-e "MINIO_ROOT_PASSWORD=wJalrXUtnFEMIK7MDENGbPxRfiCYEXAMPLEKEY" \
|
||||
-v ${HOME}/data:/data \
|
||||
minio/minio server /data
|
||||
```
|
||||
@@ -90,8 +90,8 @@ On windows you would need to use [Docker integrated windows authentication](http
|
||||
docker run -p 9000:9000 \
|
||||
--name minio1 \
|
||||
--security-opt "credentialspec=file://myuser.json"
|
||||
-e "MINIO_ACCESS_KEY=AKIAIOSFODNN7EXAMPLE" \
|
||||
-e "MINIO_SECRET_KEY=wJalrXUtnFEMIK7MDENGbPxRfiCYEXAMPLEKEY" \
|
||||
-e "MINIO_ROOT_USER=AKIAIOSFODNN7EXAMPLE" \
|
||||
-e "MINIO_ROOT_PASSWORD=wJalrXUtnFEMIK7MDENGbPxRfiCYEXAMPLEKEY" \
|
||||
-v D:\data:/data \
|
||||
minio/minio server /data
|
||||
```
|
||||
@@ -117,14 +117,14 @@ To use other secret names follow the instructions above and replace `access_key`
|
||||
docker service create --name="minio-service" \
|
||||
--secret="my_access_key" \
|
||||
--secret="my_secret_key" \
|
||||
--env="MINIO_ACCESS_KEY_FILE=my_access_key" \
|
||||
--env="MINIO_SECRET_KEY_FILE=my_secret_key" \
|
||||
--env="MINIO_ROOT_USER_FILE=my_access_key" \
|
||||
--env="MINIO_ROOT_PASSWORD_FILE=my_secret_key" \
|
||||
minio/minio server /data
|
||||
```
|
||||
`MINIO_ACCESS_KEY_FILE` and `MINIO_SECRET_KEY_FILE` also support custom absolute paths, in case Docker secrets are mounted to custom locations or other tools are used to mount secrets into the container. For example, HashiCorp Vault injects secrets to `/vault/secrets`. With the custom names above, set the environment variables to
|
||||
`MINIO_ROOT_USER_FILE` and `MINIO_ROOT_PASSWORD_FILE` also support custom absolute paths, in case Docker secrets are mounted to custom locations or other tools are used to mount secrets into the container. For example, HashiCorp Vault injects secrets to `/vault/secrets`. With the custom names above, set the environment variables to
|
||||
```
|
||||
MINIO_ACCESS_KEY_FILE=/vault/secrets/my_access_key
|
||||
MINIO_SECRET_KEY_FILE=/vault/secrets/my_secret_key
|
||||
MINIO_ROOT_USER_FILE=/vault/secrets/my_access_key
|
||||
MINIO_ROOT_PASSWORD_FILE=/vault/secrets/my_secret_key
|
||||
```
|
||||
|
||||
### Retrieving Container ID
|
||||
|
||||
@@ -5,15 +5,15 @@ MinIO Gateway adds Amazon S3 compatibility to Microsoft Azure Blob Storage.
|
||||
### Using Docker
|
||||
```
|
||||
docker run -p 9000:9000 --name azure-s3 \
|
||||
-e "MINIO_ACCESS_KEY=azurestorageaccountname" \
|
||||
-e "MINIO_SECRET_KEY=azurestorageaccountkey" \
|
||||
-e "MINIO_ROOT_USER=azurestorageaccountname" \
|
||||
-e "MINIO_ROOT_PASSWORD=azurestorageaccountkey" \
|
||||
minio/minio gateway azure
|
||||
```
|
||||
|
||||
### Using Binary
|
||||
```
|
||||
export MINIO_ACCESS_KEY=azureaccountname
|
||||
export MINIO_SECRET_KEY=azureaccountkey
|
||||
export MINIO_ROOT_USER=azureaccountname
|
||||
export MINIO_ROOT_PASSWORD=azureaccountkey
|
||||
minio gateway azure
|
||||
```
|
||||
## Test using MinIO Browser
|
||||
@@ -38,7 +38,7 @@ mc ls myazure
|
||||
|
||||
### Use custom access/secret keys
|
||||
|
||||
If you do not want to share the credentials of the Azure blob storage with your users/applications, you can set the original credentials in the shell environment using `AZURE_STORAGE_ACCOUNT` and `AZURE_STORAGE_KEY` variables and assign different access/secret keys to `MINIO_ACCESS_KEY` and `MINIO_SECRET_KEY`.
|
||||
If you do not want to share the credentials of the Azure blob storage with your users/applications, you can set the original credentials in the shell environment using `AZURE_STORAGE_ACCOUNT` and `AZURE_STORAGE_KEY` variables and assign different access/secret keys to `MINIO_ROOT_USER` and `MINIO_ROOT_PASSWORD`.
|
||||
|
||||
### Known limitations
|
||||
Gateway inherits the following Azure limitations:
|
||||
|
||||
@@ -24,8 +24,8 @@ MinIO GCS Gateway allows you to access Google Cloud Storage (GCS) with Amazon S3
|
||||
docker run -p 9000:9000 --name gcs-s3 \
|
||||
-v /path/to/credentials.json:/credentials.json \
|
||||
-e "GOOGLE_APPLICATION_CREDENTIALS=/credentials.json" \
|
||||
-e "MINIO_ACCESS_KEY=minioaccountname" \
|
||||
-e "MINIO_SECRET_KEY=minioaccountkey" \
|
||||
-e "MINIO_ROOT_USER=minioaccountname" \
|
||||
-e "MINIO_ROOT_PASSWORD=minioaccountkey" \
|
||||
minio/minio gateway gcs yourprojectid
|
||||
```
|
||||
|
||||
@@ -33,8 +33,8 @@ docker run -p 9000:9000 --name gcs-s3 \
|
||||
|
||||
```sh
|
||||
export GOOGLE_APPLICATION_CREDENTIALS=/path/to/credentials.json
|
||||
export MINIO_ACCESS_KEY=minioaccesskey
|
||||
export MINIO_SECRET_KEY=miniosecretkey
|
||||
export MINIO_ROOT_USER=minioaccesskey
|
||||
export MINIO_ROOT_PASSWORD=miniosecretkey
|
||||
minio gateway gcs yourprojectid
|
||||
```
|
||||
|
||||
|
||||
@@ -8,15 +8,15 @@ MinIO HDFS gateway adds Amazon S3 API support to Hadoop HDFS filesystem. Applica
|
||||
### Using Binary
|
||||
Namenode information is obtained by reading `core-site.xml` automatically from your hadoop environment variables *$HADOOP_HOME*
|
||||
```
|
||||
export MINIO_ACCESS_KEY=minio
|
||||
export MINIO_SECRET_KEY=minio123
|
||||
export MINIO_ROOT_USER=minio
|
||||
export MINIO_ROOT_PASSWORD=minio123
|
||||
minio gateway hdfs
|
||||
```
|
||||
|
||||
You can also override the namenode endpoint as shown below.
|
||||
```
|
||||
export MINIO_ACCESS_KEY=minio
|
||||
export MINIO_SECRET_KEY=minio123
|
||||
export MINIO_ROOT_USER=minio
|
||||
export MINIO_ROOT_PASSWORD=minio123
|
||||
minio gateway hdfs hdfs://namenode:8200
|
||||
```
|
||||
|
||||
@@ -25,8 +25,8 @@ Using docker is experimental, most Hadoop environments are not dockerized and ma
|
||||
```
|
||||
docker run -p 9000:9000 \
|
||||
--name hdfs-s3 \
|
||||
-e "MINIO_ACCESS_KEY=minio" \
|
||||
-e "MINIO_SECRET_KEY=minio123" \
|
||||
-e "MINIO_ROOT_USER=minio" \
|
||||
-e "MINIO_ROOT_PASSWORD=minio123" \
|
||||
minio/minio gateway hdfs hdfs://namenode:8200
|
||||
```
|
||||
|
||||
|
||||
@@ -10,8 +10,8 @@ Please ensure to replace `/shared/nasvol` with actual mount path.
|
||||
|
||||
```
|
||||
docker run -p 9000:9000 --name nas-s3 \
|
||||
-e "MINIO_ACCESS_KEY=minio" \
|
||||
-e "MINIO_SECRET_KEY=minio123" \
|
||||
-e "MINIO_ROOT_USER=minio" \
|
||||
-e "MINIO_ROOT_PASSWORD=minio123" \
|
||||
-v /shared/nasvol:/container/vol \
|
||||
minio/minio gateway nas /container/vol
|
||||
```
|
||||
@@ -19,8 +19,8 @@ docker run -p 9000:9000 --name nas-s3 \
|
||||
### Using Binary
|
||||
|
||||
```
|
||||
export MINIO_ACCESS_KEY=minio
|
||||
export MINIO_SECRET_KEY=minio123
|
||||
export MINIO_ROOT_USER=minio
|
||||
export MINIO_ROOT_PASSWORD=minio123
|
||||
minio gateway nas /shared/nasvol
|
||||
```
|
||||
|
||||
|
||||
@@ -8,25 +8,25 @@ As a prerequisite to run MinIO S3 gateway, you need valid AWS S3 access key and
|
||||
### Using Docker
|
||||
```
|
||||
docker run -p 9000:9000 --name minio-s3 \
|
||||
-e "MINIO_ACCESS_KEY=aws_s3_access_key" \
|
||||
-e "MINIO_SECRET_KEY=aws_s3_secret_key" \
|
||||
-e "MINIO_ROOT_USER=aws_s3_access_key" \
|
||||
-e "MINIO_ROOT_PASSWORD=aws_s3_secret_key" \
|
||||
minio/minio gateway s3
|
||||
```
|
||||
|
||||
### Using Binary
|
||||
```
|
||||
export MINIO_ACCESS_KEY=aws_s3_access_key
|
||||
export MINIO_SECRET_KEY=aws_s3_secret_key
|
||||
export MINIO_ROOT_USER=aws_s3_access_key
|
||||
export MINIO_ROOT_PASSWORD=aws_s3_secret_key
|
||||
minio gateway s3
|
||||
```
|
||||
|
||||
### Using Binary in EC2
|
||||
Using IAM rotating credentials for AWS S3
|
||||
|
||||
If you are using an S3 enabled IAM role on an EC2 instance for S3 access, MinIO will still require env vars MINIO_ACCESS_KEY and MINIO_SECRET_KEY to be set for its internal use. These may be set to any value which meets the length requirements. Access key length should be at least 3, and secret key length at least 8 characters.
|
||||
If you are using an S3 enabled IAM role on an EC2 instance for S3 access, MinIO will still require env vars MINIO_ROOT_USER and MINIO_ROOT_PASSWORD to be set for its internal use. These may be set to any value which meets the length requirements. Access key length should be at least 3, and secret key length at least 8 characters.
|
||||
```
|
||||
export MINIO_ACCESS_KEY=custom_access_key
|
||||
export MINIO_SECRET_KEY=custom_secret_key
|
||||
export MINIO_ROOT_USER=custom_access_key
|
||||
export MINIO_ROOT_PASSWORD=custom_secret_key
|
||||
minio gateway s3
|
||||
```
|
||||
|
||||
@@ -89,15 +89,15 @@ minio gateway s3
|
||||
### Using Docker
|
||||
```
|
||||
docker run -p 9000:9000 --name minio-s3 \
|
||||
-e "MINIO_ACCESS_KEY=access_key" \
|
||||
-e "MINIO_SECRET_KEY=secret_key" \
|
||||
-e "MINIO_ROOT_USER=access_key" \
|
||||
-e "MINIO_ROOT_PASSWORD=secret_key" \
|
||||
minio/minio gateway s3 https://s3_compatible_service_endpoint:port
|
||||
```
|
||||
|
||||
### Using Binary
|
||||
```
|
||||
export MINIO_ACCESS_KEY=access_key
|
||||
export MINIO_SECRET_KEY=secret_key
|
||||
export MINIO_ROOT_USER=access_key
|
||||
export MINIO_ROOT_PASSWORD=secret_key
|
||||
minio gateway s3 https://s3_compatible_service_endpoint:port
|
||||
```
|
||||
|
||||
|
||||
@@ -27,8 +27,8 @@ export MINIO_KMS_KES_KEY_NAME=my-minio-key
|
||||
#### 3. Start the MinIO Server
|
||||
|
||||
```sh
|
||||
export MINIO_ACCESS_KEY=minio
|
||||
export MINIO_SECRET_KEY=minio123
|
||||
export MINIO_ROOT_USER=minio
|
||||
export MINIO_ROOT_PASSWORD=minio123
|
||||
minio server ~/export
|
||||
```
|
||||
|
||||
|
||||
@@ -43,16 +43,16 @@ To host multiple tenants in a distributed environment, run several distributed M
|
||||
Use the following commands to host 3 tenants on a 4-node distributed configuration:
|
||||
|
||||
```sh
|
||||
export MINIO_ACCESS_KEY=<TENANT1_ACCESS_KEY>
|
||||
export MINIO_SECRET_KEY=<TENANT1_SECRET_KEY>
|
||||
export MINIO_ROOT_USER=<TENANT1_ACCESS_KEY>
|
||||
export MINIO_ROOT_PASSWORD=<TENANT1_SECRET_KEY>
|
||||
minio server --address :9001 http://192.168.10.1{1...4}/data/tenant1
|
||||
|
||||
export MINIO_ACCESS_KEY=<TENANT2_ACCESS_KEY>
|
||||
export MINIO_SECRET_KEY=<TENANT2_SECRET_KEY>
|
||||
export MINIO_ROOT_USER=<TENANT2_ACCESS_KEY>
|
||||
export MINIO_ROOT_PASSWORD=<TENANT2_SECRET_KEY>
|
||||
minio server --address :9002 http://192.168.10.1{1...4}/data/tenant2
|
||||
|
||||
export MINIO_ACCESS_KEY=<TENANT3_ACCESS_KEY>
|
||||
export MINIO_SECRET_KEY=<TENANT3_SECRET_KEY>
|
||||
export MINIO_ROOT_USER=<TENANT3_ACCESS_KEY>
|
||||
export MINIO_ROOT_PASSWORD=<TENANT3_SECRET_KEY>
|
||||
minio server --address :9003 http://192.168.10.1{1...4}/data/tenant3
|
||||
```
|
||||
|
||||
@@ -60,7 +60,7 @@ minio server --address :9003 http://192.168.10.1{1...4}/data/tenant3
|
||||
|
||||
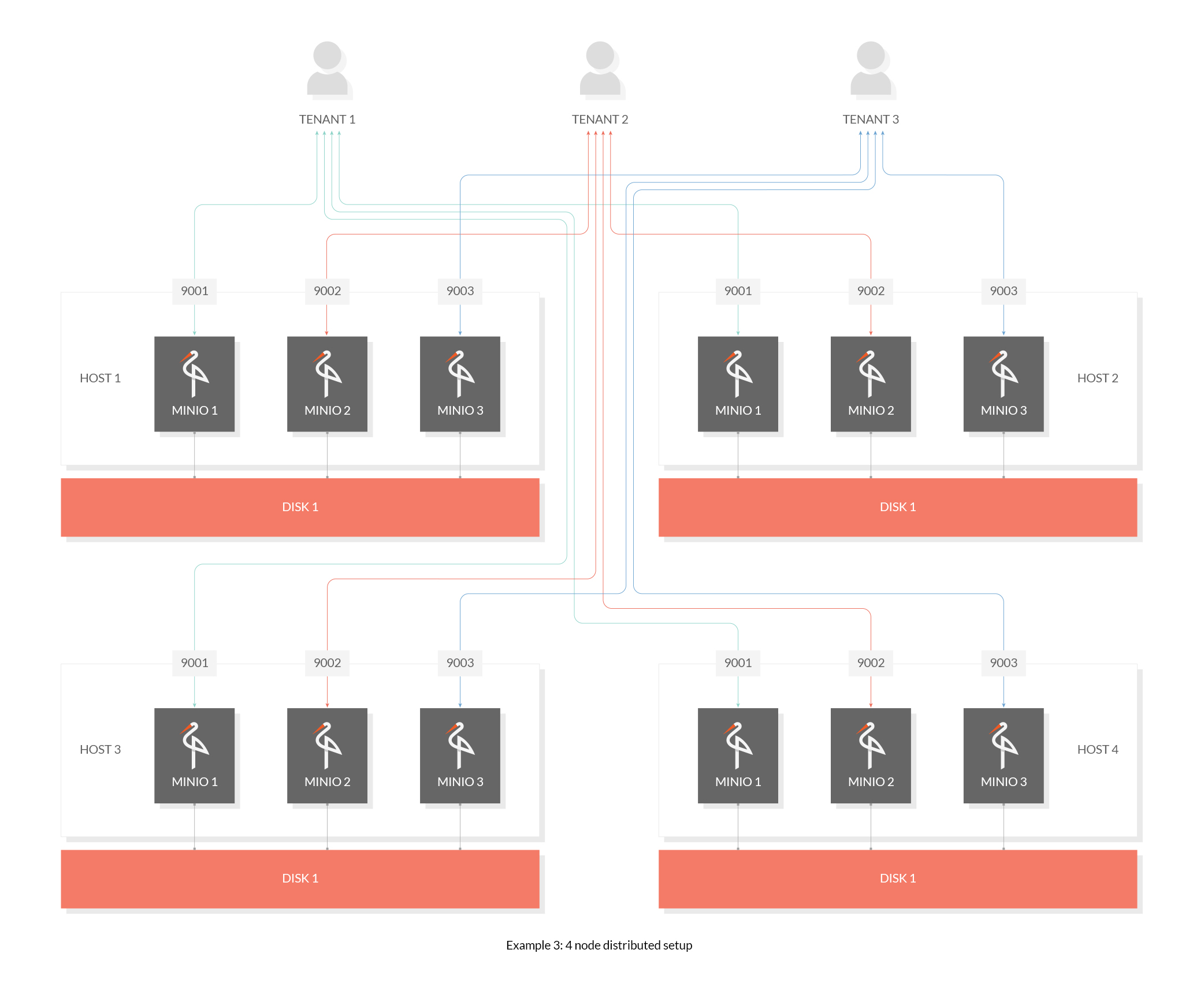
|
||||
|
||||
**Note**: On distributed systems, credentials must be defined and exported using the `MINIO_ACCESS_KEY` and `MINIO_SECRET_KEY` environment variables. If a domain is required, it must be specified by defining and exporting the `MINIO_DOMAIN` environment variable.
|
||||
**Note**: On distributed systems, credentials must be defined and exported using the `MINIO_ROOT_USER` and `MINIO_ROOT_PASSWORD` environment variables. If a domain is required, it must be specified by defining and exporting the `MINIO_DOMAIN` environment variable.
|
||||
|
||||
## <a name="cloud-scale-deployment"></a>Cloud Scale Deployment
|
||||
|
||||
|
||||
@@ -12,8 +12,8 @@ services:
|
||||
expose:
|
||||
- "9000"
|
||||
environment:
|
||||
MINIO_ACCESS_KEY: minio
|
||||
MINIO_SECRET_KEY: minio123
|
||||
MINIO_ROOT_USER: minio
|
||||
MINIO_ROOT_PASSWORD: minio123
|
||||
command: server http://minio{1...4}/data{1...2}
|
||||
healthcheck:
|
||||
test: ["CMD", "curl", "-f", "http://localhost:9000/minio/health/live"]
|
||||
@@ -29,8 +29,8 @@ services:
|
||||
expose:
|
||||
- "9000"
|
||||
environment:
|
||||
MINIO_ACCESS_KEY: minio
|
||||
MINIO_SECRET_KEY: minio123
|
||||
MINIO_ROOT_USER: minio
|
||||
MINIO_ROOT_PASSWORD: minio123
|
||||
command: server http://minio{1...4}/data{1...2}
|
||||
healthcheck:
|
||||
test: ["CMD", "curl", "-f", "http://localhost:9000/minio/health/live"]
|
||||
@@ -46,8 +46,8 @@ services:
|
||||
expose:
|
||||
- "9000"
|
||||
environment:
|
||||
MINIO_ACCESS_KEY: minio
|
||||
MINIO_SECRET_KEY: minio123
|
||||
MINIO_ROOT_USER: minio
|
||||
MINIO_ROOT_PASSWORD: minio123
|
||||
command: server http://minio{1...4}/data{1...2}
|
||||
healthcheck:
|
||||
test: ["CMD", "curl", "-f", "http://localhost:9000/minio/health/live"]
|
||||
@@ -63,8 +63,8 @@ services:
|
||||
expose:
|
||||
- "9000"
|
||||
environment:
|
||||
MINIO_ACCESS_KEY: minio
|
||||
MINIO_SECRET_KEY: minio123
|
||||
MINIO_ROOT_USER: minio
|
||||
MINIO_ROOT_PASSWORD: minio123
|
||||
command: server http://minio{1...4}/data{1...2}
|
||||
healthcheck:
|
||||
test: ["CMD", "curl", "-f", "http://localhost:9000/minio/health/live"]
|
||||
|
||||
@@ -15,8 +15,8 @@ services:
|
||||
aliases:
|
||||
- minio-cluster
|
||||
environment:
|
||||
MINIO_ACCESS_KEY: AKIAIOSFODNN7EXAMPLE
|
||||
MINIO_SECRET_KEY: wJalrXUtnFEMI/K7MDENG/bPxRfiCYEXAMPLEKEY
|
||||
MINIO_ROOT_USER: AKIAIOSFODNN7EXAMPLE
|
||||
MINIO_ROOT_PASSWORD: wJalrXUtnFEMI/K7MDENG/bPxRfiCYEXAMPLEKEY
|
||||
deploy:
|
||||
restart_policy:
|
||||
delay: 10s
|
||||
@@ -46,8 +46,8 @@ services:
|
||||
aliases:
|
||||
- minio-cluster
|
||||
environment:
|
||||
MINIO_ACCESS_KEY: AKIAIOSFODNN7EXAMPLE
|
||||
MINIO_SECRET_KEY: wJalrXUtnFEMI/K7MDENG/bPxRfiCYEXAMPLEKEY
|
||||
MINIO_ROOT_USER: AKIAIOSFODNN7EXAMPLE
|
||||
MINIO_ROOT_PASSWORD: wJalrXUtnFEMI/K7MDENG/bPxRfiCYEXAMPLEKEY
|
||||
deploy:
|
||||
restart_policy:
|
||||
delay: 10s
|
||||
@@ -77,8 +77,8 @@ services:
|
||||
aliases:
|
||||
- minio-cluster
|
||||
environment:
|
||||
MINIO_ACCESS_KEY: AKIAIOSFODNN7EXAMPLE
|
||||
MINIO_SECRET_KEY: wJalrXUtnFEMI/K7MDENG/bPxRfiCYEXAMPLEKEY
|
||||
MINIO_ROOT_USER: AKIAIOSFODNN7EXAMPLE
|
||||
MINIO_ROOT_PASSWORD: wJalrXUtnFEMI/K7MDENG/bPxRfiCYEXAMPLEKEY
|
||||
deploy:
|
||||
restart_policy:
|
||||
delay: 10s
|
||||
@@ -108,8 +108,8 @@ services:
|
||||
aliases:
|
||||
- minio-cluster
|
||||
environment:
|
||||
MINIO_ACCESS_KEY: AKIAIOSFODNN7EXAMPLE
|
||||
MINIO_SECRET_KEY: wJalrXUtnFEMI/K7MDENG/bPxRfiCYEXAMPLEKEY
|
||||
MINIO_ROOT_USER: AKIAIOSFODNN7EXAMPLE
|
||||
MINIO_ROOT_PASSWORD: wJalrXUtnFEMI/K7MDENG/bPxRfiCYEXAMPLEKEY
|
||||
deploy:
|
||||
restart_policy:
|
||||
delay: 10s
|
||||
|
||||
@@ -34,8 +34,8 @@ To run MinIO shared backend instances, you need to start multiple MinIO servers
|
||||
You'll need the path to the shared volume, e.g. `/path/to/nfs-volume`. Then run the following commands on all the nodes you'd like to launch MinIO.
|
||||
|
||||
```sh
|
||||
export MINIO_ACCESS_KEY=<ACCESS_KEY>
|
||||
export MINIO_SECRET_KEY=<SECRET_KEY>
|
||||
export MINIO_ROOT_USER=<ACCESS_KEY>
|
||||
export MINIO_ROOT_PASSWORD=<SECRET_KEY>
|
||||
minio gateway nas /path/to/nfs-volume
|
||||
```
|
||||
|
||||
@@ -44,8 +44,8 @@ minio gateway nas /path/to/nfs-volume
|
||||
You'll need the path to the shared volume, e.g. `\\remote-server\smb`. Then run the following commands on all the nodes you'd like to launch MinIO.
|
||||
|
||||
```cmd
|
||||
set MINIO_ACCESS_KEY=my-username
|
||||
set MINIO_SECRET_KEY=my-password
|
||||
set MINIO_ROOT_USER=my-username
|
||||
set MINIO_ROOT_PASSWORD=my-password
|
||||
minio.exe gateway nas \\remote-server\smb\export
|
||||
```
|
||||
|
||||
@@ -54,8 +54,8 @@ minio.exe gateway nas \\remote-server\smb\export
|
||||
If a remote volume, e.g. `\\remote-server\smb` is mounted as a drive, e.g. `M:\`. You can use [`net use`](https://technet.microsoft.com/en-us/library/bb490717.aspx) command to map the drive to a folder.
|
||||
|
||||
```cmd
|
||||
set MINIO_ACCESS_KEY=my-username
|
||||
set MINIO_SECRET_KEY=my-password
|
||||
set MINIO_ROOT_USER=my-username
|
||||
set MINIO_ROOT_PASSWORD=my-password
|
||||
net use m: \\remote-server\smb\export /P:Yes
|
||||
minio.exe gateway nas M:\export
|
||||
```
|
||||
|
||||
@@ -43,8 +43,8 @@ In this document we will explain in detail on how to configure all the prerequis
|
||||
Make sure we have followed the previous step and configured each software independently, once done we can now proceed to use MinIO STS API and MinIO server to use these credentials to perform object API operations.
|
||||
|
||||
```
|
||||
export MINIO_ACCESS_KEY=minio
|
||||
export MINIO_SECRET_KEY=minio123
|
||||
export MINIO_ROOT_USER=minio
|
||||
export MINIO_ROOT_PASSWORD=minio123
|
||||
export MINIO_IDENTITY_OPENID_CONFIG_URL=http://localhost:8080/auth/realms/demo/.well-known/openid-configuration
|
||||
export MINIO_IDENTITY_OPENID_CLIENT_ID="843351d4-1080-11ea-aa20-271ecba3924a"
|
||||
minio server /mnt/data
|
||||
@@ -56,8 +56,8 @@ Make sure we have followed the previous step and configured each software indepe
|
||||
> NOTE: MinIO gateway requires etcd to be configured to use STS API.
|
||||
|
||||
```
|
||||
export MINIO_ACCESS_KEY=aws_access_key
|
||||
export MINIO_SECRET_KEY=aws_secret_key
|
||||
export MINIO_ROOT_USER=aws_access_key
|
||||
export MINIO_ROOT_PASSWORD=aws_secret_key
|
||||
export MINIO_IDENTITY_OPENID_CONFIG_URL=http://localhost:8080/auth/realms/demo/.well-known/openid-configuration
|
||||
export MINIO_IDENTITY_OPENID_CLIENT_ID="843351d4-1080-11ea-aa20-271ecba3924a"
|
||||
export MINIO_ETCD_ENDPOINTS=http://localhost:2379
|
||||
|
||||
@@ -91,8 +91,8 @@ http://minio:9000/?Action=AssumeRole&DurationSeconds=3600&Version=2011-06-15&Pol
|
||||
|
||||
## Using AssumeRole API
|
||||
```
|
||||
$ export MINIO_ACCESS_KEY=minio
|
||||
$ export MINIO_SECRET_KEY=minio123
|
||||
$ export MINIO_ROOT_USER=minio
|
||||
$ export MINIO_ROOT_PASSWORD=minio123
|
||||
$ minio server ~/test
|
||||
```
|
||||
|
||||
|
||||
@@ -92,8 +92,8 @@ http://minio.cluster:9000?Action=AssumeRoleWithClientGrants&DurationSeconds=3600
|
||||
|
||||
## Using ClientGrants API
|
||||
```
|
||||
export MINIO_ACCESS_KEY=minio
|
||||
export MINIO_SECRET_KEY=minio123
|
||||
export MINIO_ROOT_USER=minio
|
||||
export MINIO_ROOT_PASSWORD=minio123
|
||||
export MINIO_IDENTITY_OPENID_CONFIG_URL=http://localhost:8080/auth/realms/demo/.well-known/openid-configuration
|
||||
export MINIO_IDENTITY_OPENID_CLIENT_ID="843351d4-1080-11ea-aa20-271ecba3924a"
|
||||
minio server /mnt/export
|
||||
|
||||
@@ -38,8 +38,8 @@ Configure and install keycloak server by following [Keycloak Installation Guide]
|
||||
|
||||
### Configure MinIO
|
||||
```
|
||||
$ export MINIO_ACCESS_KEY=minio
|
||||
$ export MINIO_SECRET_KEY=minio123
|
||||
$ export MINIO_ROOT_USER=minio
|
||||
$ export MINIO_ROOT_PASSWORD=minio123
|
||||
$ minio server /mnt/export
|
||||
```
|
||||
|
||||
|
||||
@@ -215,8 +215,8 @@ http://minio.cluster:9000?Action=AssumeRoleWithLDAPIdentity&LDAPUsername=foouser
|
||||
|
||||
With multiple OU hierarchies for users, and multiple group search base DN's.
|
||||
```
|
||||
$ export MINIO_ACCESS_KEY=minio
|
||||
$ export MINIO_SECRET_KEY=minio123
|
||||
$ export MINIO_ROOT_USER=minio
|
||||
$ export MINIO_ROOT_PASSWORD=minio123
|
||||
$ export MINIO_IDENTITY_LDAP_SERVER_ADDR='my.ldap-active-dir-server.com:636'
|
||||
$ export MINIO_IDENTITY_LDAP_USERNAME_FORMAT='cn=%s,ou=Users,ou=BUS1,ou=LOB,dc=somedomain,dc=com;cn=%s,ou=Users,ou=BUS2,ou=LOB,dc=somedomain,dc=com'
|
||||
$ export MINIO_IDENTITY_LDAP_GROUP_SEARCH_BASE_DN='dc=minioad,dc=local;dc=somedomain,dc=com'
|
||||
|
||||
@@ -92,8 +92,8 @@ http://minio.cluster:9000?Action=AssumeRoleWithWebIdentity&DurationSeconds=3600&
|
||||
|
||||
## Using WebIdentity API
|
||||
```
|
||||
export MINIO_ACCESS_KEY=minio
|
||||
export MINIO_SECRET_KEY=minio123
|
||||
export MINIO_ROOT_USER=minio
|
||||
export MINIO_ROOT_PASSWORD=minio123
|
||||
export MINIO_IDENTITY_OPENID_CONFIG_URL=https://accounts.google.com/.well-known/openid-configuration
|
||||
export MINIO_IDENTITY_OPENID_CLIENT_ID="843351d4-1080-11ea-aa20-271ecba3924a"
|
||||
# Optional: Allow to specify the requested OpenID scopes (OpenID only requires the `openid` scope)
|
||||
|
||||
@@ -15,8 +15,8 @@ Example: Limit a MinIO cluster to accept at max 1600 simultaneous S3 API request
|
||||
|
||||
```sh
|
||||
export MINIO_API_REQUESTS_MAX=1600
|
||||
export MINIO_ACCESS_KEY=your-access-key
|
||||
export MINIO_SECRET_KEY=your-secret-key
|
||||
export MINIO_ROOT_USER=your-access-key
|
||||
export MINIO_ROOT_PASSWORD=your-secret-key
|
||||
minio server http://server{1...8}/mnt/hdd{1...16}
|
||||
```
|
||||
|
||||
@@ -39,8 +39,8 @@ Example: Limit a MinIO cluster to accept at max 1600 simultaneous S3 API request
|
||||
```sh
|
||||
export MINIO_API_REQUESTS_MAX=1600
|
||||
export MINIO_API_REQUESTS_DEADLINE=2m
|
||||
export MINIO_ACCESS_KEY=your-access-key
|
||||
export MINIO_SECRET_KEY=your-secret-key
|
||||
export MINIO_ROOT_USER=your-access-key
|
||||
export MINIO_ROOT_PASSWORD=your-secret-key
|
||||
minio server http://server{1...8}/mnt/hdd{1...16}
|
||||
```
|
||||
|
||||
|
||||
@@ -37,11 +37,11 @@ $ mc tree --files ~/.minio
|
||||
你可以使用`--certs-dir`命令行选项提供自定义certs目录。
|
||||
|
||||
#### 凭据
|
||||
只能通过环境变量`MINIO_ACCESS_KEY` 和 `MINIO_SECRET_KEY` 更改MinIO的admin凭据和root凭据。使用这两个值的组合,MinIO加密存储在后端的配置
|
||||
只能通过环境变量`MINIO_ROOT_USER` 和 `MINIO_ROOT_PASSWORD` 更改MinIO的admin凭据和root凭据。使用这两个值的组合,MinIO加密存储在后端的配置
|
||||
|
||||
```
|
||||
export MINIO_ACCESS_KEY=minio
|
||||
export MINIO_SECRET_KEY=minio13
|
||||
export MINIO_ROOT_USER=minio
|
||||
export MINIO_ROOT_PASSWORD=minio13
|
||||
minio server /data
|
||||
```
|
||||
|
||||
@@ -52,16 +52,16 @@ minio server /data
|
||||
> 旧的环境变量永远不会在内存中被记住,并且在使用新凭据迁移现有内容后立即销毁。在服务器再次成功重启后,你可以安全的删除它们。
|
||||
|
||||
```
|
||||
export MINIO_ACCESS_KEY=newminio
|
||||
export MINIO_SECRET_KEY=newminio123
|
||||
export MINIO_ACCESS_KEY_OLD=minio
|
||||
export MINIO_SECRET_KEY_OLD=minio123
|
||||
export MINIO_ROOT_USER=newminio
|
||||
export MINIO_ROOT_PASSWORD=newminio123
|
||||
export MINIO_ROOT_USER_OLD=minio
|
||||
export MINIO_ROOT_PASSWORD_OLD=minio123
|
||||
minio server /data
|
||||
```
|
||||
|
||||
迁移完成后, 服务器会自动的取消进程空间中的`MINIO_ACCESS_KEY_OLD` and `MINIO_SECRET_KEY_OLD`设置。
|
||||
迁移完成后, 服务器会自动的取消进程空间中的`MINIO_ROOT_USER_OLD` and `MINIO_ROOT_PASSWORD_OLD`设置。
|
||||
|
||||
> **注意: 在下一次服务重新启动前,要确保移除脚本或者服务文件中的 `MINIO_ACCESS_KEY_OLD` and `MINIO_SECRET_KEY_OLD`, 避免现有的内容被双重加密**
|
||||
> **注意: 在下一次服务重新启动前,要确保移除脚本或者服务文件中的 `MINIO_ROOT_USER_OLD` and `MINIO_ROOT_PASSWORD_OLD`, 避免现有的内容被双重加密**
|
||||
|
||||
#### 区域
|
||||
```
|
||||
|
||||
@@ -43,7 +43,7 @@ mkfs.xfs /tmp/data # build xfs filesystem on /tmp/data
|
||||
sudo mkdir /mnt/cache # create mount dir
|
||||
sudo mount -o relatime /tmp/data /mnt/cache # mount xfs on /mnt/cache with atime.
|
||||
docker pull minio/minio
|
||||
docker run --net=host -e MINIO_ACCESS_KEY={s3-access-key} -e MINIO_SECRET_KEY={s3-secret-key} -e MINIO_CACHE_DRIVES=/cache -e MINIO_CACHE_QUOTA=99 -e MINIO_CACHE_AFTER=0 -e MINIO_CACHE_WATERMARK_LOW=90 -e MINIO_CACHE_WATERMARK_HIGH=95 -v /mnt/cache:/cache minio/minio:latest gateway s3
|
||||
docker run --net=host -e MINIO_ROOT_USER={s3-access-key} -e MINIO_ROOT_PASSWORD={s3-secret-key} -e MINIO_CACHE_DRIVES=/cache -e MINIO_CACHE_QUOTA=99 -e MINIO_CACHE_AFTER=0 -e MINIO_CACHE_WATERMARK_LOW=90 -e MINIO_CACHE_WATERMARK_HIGH=95 -v /mnt/cache:/cache minio/minio:latest gateway s3
|
||||
|
||||
```
|
||||
|
||||
|
||||
@@ -39,7 +39,7 @@ Minio在分布式和单机模式下,所有读写操作都严格遵守**read-af
|
||||
|
||||
*注意*
|
||||
|
||||
- 分布式Minio里所有的节点需要有同样的access秘钥和secret秘钥,这样这些节点才能建立联接。为了实现这个,__建议__ 在执行minio server命令之前,在所有节点上先将access秘钥和secret秘钥export成环境变量`MINIO_ACCESS_KEY` 和 `MINIO_SECRET_KEY`。
|
||||
- 分布式Minio里所有的节点需要有同样的access秘钥和secret秘钥,这样这些节点才能建立联接。为了实现这个,__建议__ 在执行minio server命令之前,在所有节点上先将access秘钥和secret秘钥export成环境变量`MINIO_ROOT_USER` 和 `MINIO_ROOT_PASSWORD`。
|
||||
- __MinIO 可创建每组4到16个磁盘组成的纠删码集合。所以你提供的磁盘总数必须是其中一个数字的倍数。__
|
||||
- MinIO会根据给定的磁盘总数或者节点总数选择最大的纠删码集合大小,确保统一分布,即每个节点参与每个集合的磁盘数量相等。
|
||||
- __每个对象被写入一个EC集合中,因此该对象分布在不超过16个磁盘上。__
|
||||
@@ -58,8 +58,8 @@ Minio在分布式和单机模式下,所有读写操作都严格遵守**read-af
|
||||
#### GNU/Linux 和 macOS
|
||||
|
||||
```shell
|
||||
export MINIO_ACCESS_KEY=<ACCESS_KEY>
|
||||
export MINIO_SECRET_KEY=<SECRET_KEY>
|
||||
export MINIO_ROOT_USER=<ACCESS_KEY>
|
||||
export MINIO_ROOT_PASSWORD=<SECRET_KEY>
|
||||
minio server http://host{1...n}/export{1...m}
|
||||
```
|
||||
|
||||
@@ -71,8 +71,8 @@ minio server http://host{1...n}/export{1...m}
|
||||
MinIO支持通过命令,指定新的集群来扩展现有集群(纠删码模式),命令行如下:
|
||||
|
||||
```sh
|
||||
export MINIO_ACCESS_KEY=<ACCESS_KEY>
|
||||
export MINIO_SECRET_KEY=<SECRET_KEY>
|
||||
export MINIO_ROOT_USER=<ACCESS_KEY>
|
||||
export MINIO_ROOT_PASSWORD=<SECRET_KEY>
|
||||
minio server http://host{1...n}/export{1...m} http://host{o...z}/export{1...m}
|
||||
```
|
||||
|
||||
|
||||
@@ -8,8 +8,8 @@ MinIO 需要一个持久卷来存储配置和应用数据。不过, 如果只是
|
||||
|
||||
```sh
|
||||
docker run -p 9000:9000 \
|
||||
-e "MINIO_ACCESS_KEY=AKIAIOSFODNN7EXAMPLE" \
|
||||
-e "MINIO_SECRET_KEY=wJalrXUtnFEMI/K7MDENG/bPxRfiCYEXAMPLEKEY" \
|
||||
-e "MINIO_ROOT_USER=AKIAIOSFODNN7EXAMPLE" \
|
||||
-e "MINIO_ROOT_PASSWORD=wJalrXUtnFEMI/K7MDENG/bPxRfiCYEXAMPLEKEY" \
|
||||
minio/minio server /data
|
||||
```
|
||||
|
||||
@@ -20,8 +20,8 @@ docker run -p 9000:9000 \
|
||||
docker run -p 9000:9000 \
|
||||
--name minio1 \
|
||||
-v /mnt/data:/data \
|
||||
-e "MINIO_ACCESS_KEY=AKIAIOSFODNN7EXAMPLE" \
|
||||
-e "MINIO_SECRET_KEY=wJalrXUtnFEMI/K7MDENG/bPxRfiCYEXAMPLEKEY" \
|
||||
-e "MINIO_ROOT_USER=AKIAIOSFODNN7EXAMPLE" \
|
||||
-e "MINIO_ROOT_PASSWORD=wJalrXUtnFEMI/K7MDENG/bPxRfiCYEXAMPLEKEY" \
|
||||
minio/minio server /data
|
||||
```
|
||||
|
||||
@@ -30,8 +30,8 @@ docker run -p 9000:9000 \
|
||||
docker run -p 9000:9000 \
|
||||
--name minio1 \
|
||||
-v D:\data:/data \
|
||||
-e "MINIO_ACCESS_KEY=AKIAIOSFODNN7EXAMPLE" \
|
||||
-e "MINIO_SECRET_KEY=wJalrXUtnFEMI/K7MDENG/bPxRfiCYEXAMPLEKEY" \
|
||||
-e "MINIO_ROOT_USER=AKIAIOSFODNN7EXAMPLE" \
|
||||
-e "MINIO_ROOT_PASSWORD=wJalrXUtnFEMI/K7MDENG/bPxRfiCYEXAMPLEKEY" \
|
||||
minio/minio server /data
|
||||
```
|
||||
|
||||
@@ -48,8 +48,8 @@ docker run -p 9000:9000 \
|
||||
#### GNU/Linux 和 macOS
|
||||
```sh
|
||||
docker run -p 9000:9000 --name minio1 \
|
||||
-e "MINIO_ACCESS_KEY=AKIAIOSFODNN7EXAMPLE" \
|
||||
-e "MINIO_SECRET_KEY=wJalrXUtnFEMI/K7MDENG/bPxRfiCYEXAMPLEKEY" \
|
||||
-e "MINIO_ROOT_USER=AKIAIOSFODNN7EXAMPLE" \
|
||||
-e "MINIO_ROOT_PASSWORD=wJalrXUtnFEMI/K7MDENG/bPxRfiCYEXAMPLEKEY" \
|
||||
-v /mnt/data:/data \
|
||||
minio/minio server /data
|
||||
```
|
||||
@@ -57,8 +57,8 @@ docker run -p 9000:9000 --name minio1 \
|
||||
#### Windows
|
||||
```powershell
|
||||
docker run -p 9000:9000 --name minio1 \
|
||||
-e "MINIO_ACCESS_KEY=AKIAIOSFODNN7EXAMPLE" \
|
||||
-e "MINIO_SECRET_KEY=wJalrXUtnFEMI/K7MDENG/bPxRfiCYEXAMPLEKEY" \
|
||||
-e "MINIO_ROOT_USER=AKIAIOSFODNN7EXAMPLE" \
|
||||
-e "MINIO_ROOT_PASSWORD=wJalrXUtnFEMI/K7MDENG/bPxRfiCYEXAMPLEKEY" \
|
||||
-v D:\data:/data \
|
||||
minio/minio server /data
|
||||
```
|
||||
@@ -75,8 +75,8 @@ mkdir -p ${HOME}/data
|
||||
docker run -p 9000:9000 \
|
||||
--user $(id -u):$(id -g) \
|
||||
--name minio1 \
|
||||
-e "MINIO_ACCESS_KEY=AKIAIOSFODNN7EXAMPLE" \
|
||||
-e "MINIO_SECRET_KEY=wJalrXUtnFEMIK7MDENGbPxRfiCYEXAMPLEKEY" \
|
||||
-e "MINIO_ROOT_USER=AKIAIOSFODNN7EXAMPLE" \
|
||||
-e "MINIO_ROOT_PASSWORD=wJalrXUtnFEMIK7MDENGbPxRfiCYEXAMPLEKEY" \
|
||||
-v ${HOME}/data:/data \
|
||||
minio/minio server /data
|
||||
```
|
||||
@@ -90,8 +90,8 @@ docker run -p 9000:9000 \
|
||||
docker run -p 9000:9000 \
|
||||
--name minio1 \
|
||||
--security-opt "credentialspec=file://myuser.json"
|
||||
-e "MINIO_ACCESS_KEY=AKIAIOSFODNN7EXAMPLE" \
|
||||
-e "MINIO_SECRET_KEY=wJalrXUtnFEMIK7MDENGbPxRfiCYEXAMPLEKEY" \
|
||||
-e "MINIO_ROOT_USER=AKIAIOSFODNN7EXAMPLE" \
|
||||
-e "MINIO_ROOT_PASSWORD=wJalrXUtnFEMIK7MDENGbPxRfiCYEXAMPLEKEY" \
|
||||
-v D:\data:/data \
|
||||
minio/minio server /data
|
||||
```
|
||||
@@ -117,8 +117,8 @@ docker service create --name="minio-service" --secret="access_key" --secret="sec
|
||||
docker service create --name="minio-service" \
|
||||
--secret="my_access_key" \
|
||||
--secret="my_secret_key" \
|
||||
--env="MINIO_ACCESS_KEY_FILE=my_access_key" \
|
||||
--env="MINIO_SECRET_KEY_FILE=my_secret_key" \
|
||||
--env="MINIO_ROOT_USER_FILE=my_access_key" \
|
||||
--env="MINIO_ROOT_PASSWORD_FILE=my_secret_key" \
|
||||
minio/minio server /data
|
||||
```
|
||||
|
||||
|
||||
@@ -6,15 +6,15 @@ MinIO网关将亚马逊S3兼容性添加到微软Azure Blob存储。
|
||||
### 使用Docker
|
||||
```
|
||||
docker run -p 9000:9000 --name azure-s3 \
|
||||
-e "MINIO_ACCESS_KEY=azureaccountname" \
|
||||
-e "MINIO_SECRET_KEY=azureaccountkey" \
|
||||
-e "MINIO_ROOT_USER=azureaccountname" \
|
||||
-e "MINIO_ROOT_PASSWORD=azureaccountkey" \
|
||||
minio/minio gateway azure
|
||||
```
|
||||
|
||||
### 使用二进制
|
||||
```
|
||||
export MINIO_ACCESS_KEY=azureaccountname
|
||||
export MINIO_SECRET_KEY=azureaccountkey
|
||||
export MINIO_ROOT_USER=azureaccountname
|
||||
export MINIO_ROOT_PASSWORD=azureaccountkey
|
||||
minio gateway azure
|
||||
```
|
||||
## 使用MinIO浏览器验证
|
||||
|
||||
@@ -18,16 +18,16 @@ MinIO GCS网关将亚马逊S3兼容性添加到Google云存储。
|
||||
docker run -p 9000:9000 --name gcs-s3 \
|
||||
-v /path/to/credentials.json:/credentials.json \
|
||||
-e "GOOGLE_APPLICATION_CREDENTIALS=/credentials.json" \
|
||||
-e "MINIO_ACCESS_KEY=minioaccountname" \
|
||||
-e "MINIO_SECRET_KEY=minioaccountkey" \
|
||||
-e "MINIO_ROOT_USER=minioaccountname" \
|
||||
-e "MINIO_ROOT_PASSWORD=minioaccountkey" \
|
||||
minio/minio gateway gcs yourprojectid
|
||||
```
|
||||
|
||||
### 使用二进制
|
||||
```
|
||||
export GOOGLE_APPLICATION_CREDENTIALS=/path/to/credentials.json
|
||||
export MINIO_ACCESS_KEY=minioaccesskey
|
||||
export MINIO_SECRET_KEY=miniosecretkey
|
||||
export MINIO_ROOT_USER=minioaccesskey
|
||||
export MINIO_ROOT_PASSWORD=miniosecretkey
|
||||
minio gateway gcs yourprojectid
|
||||
```
|
||||
|
||||
|
||||
@@ -5,15 +5,15 @@ MinIO网关使用NAS存储支持Amazon S3。你可以在同一个共享NAS卷上
|
||||
### 使用Docker
|
||||
```
|
||||
docker run -p 9000:9000 --name nas-s3 \
|
||||
-e "MINIO_ACCESS_KEY=minio" \
|
||||
-e "MINIO_SECRET_KEY=minio123" \
|
||||
-e "MINIO_ROOT_USER=minio" \
|
||||
-e "MINIO_ROOT_PASSWORD=minio123" \
|
||||
minio/minio gateway nas /shared/nasvol
|
||||
```
|
||||
|
||||
### 使用二进制
|
||||
```
|
||||
export MINIO_ACCESS_KEY=minioaccesskey
|
||||
export MINIO_SECRET_KEY=miniosecretkey
|
||||
export MINIO_ROOT_USER=minioaccesskey
|
||||
export MINIO_ROOT_PASSWORD=miniosecretkey
|
||||
minio gateway nas /shared/nasvol
|
||||
```
|
||||
## 使用浏览器进行验证
|
||||
|
||||
@@ -22,8 +22,8 @@ MinIO的纠删码功能限制了最多只能使用16块磁盘。这就限制了
|
||||
你需要有多块磁盘,例如 `/export1, /export2 .... /export24`。 然后在你想要启动MinIO的所有节点上运行以下命令。
|
||||
|
||||
```sh
|
||||
export MINIO_ACCESS_KEY=<ACCESS_KEY>
|
||||
export MINIO_SECRET_KEY=<SECRET_KEY>
|
||||
export MINIO_ROOT_USER=<ACCESS_KEY>
|
||||
export MINIO_ROOT_PASSWORD=<SECRET_KEY>
|
||||
minio server /export{1...24}
|
||||
```
|
||||
|
||||
@@ -31,8 +31,8 @@ minio server /export{1...24}
|
||||
你需要有多块在不同服务器上的磁盘,例如`http://host1/export1, http://host2/export2 .... http://host4/export16`。 然后在你想要启动MinIO的所有节点上运行以下命令。
|
||||
|
||||
```sh
|
||||
export MINIO_ACCESS_KEY=<ACCESS_KEY>
|
||||
export MINIO_SECRET_KEY=<SECRET_KEY>
|
||||
export MINIO_ROOT_USER=<ACCESS_KEY>
|
||||
export MINIO_ROOT_PASSWORD=<SECRET_KEY>
|
||||
minio server http://host{1...4}/export{1...16}
|
||||
```
|
||||
|
||||
|
||||
@@ -33,16 +33,16 @@ minio --config-dir ~/tenant3 server --address :9003 /disk1/data/tenant3 /disk2/d
|
||||
以下示例在一个4节点集群中托管三个租户。在4个节点里都执行下列命令:
|
||||
|
||||
```sh
|
||||
export MINIO_ACCESS_KEY=<TENANT1_ACCESS_KEY>
|
||||
export MINIO_SECRET_KEY=<TENANT1_SECRET_KEY>
|
||||
export MINIO_ROOT_USER=<TENANT1_ACCESS_KEY>
|
||||
export MINIO_ROOT_PASSWORD=<TENANT1_SECRET_KEY>
|
||||
minio --config-dir ~/tenant1 server --address :9001 http://192.168.10.11/data/tenant1 http://192.168.10.12/data/tenant1 http://192.168.10.13/data/tenant1 http://192.168.10.14/data/tenant1
|
||||
|
||||
export MINIO_ACCESS_KEY=<TENANT2_ACCESS_KEY>
|
||||
export MINIO_SECRET_KEY=<TENANT2_SECRET_KEY>
|
||||
export MINIO_ROOT_USER=<TENANT2_ACCESS_KEY>
|
||||
export MINIO_ROOT_PASSWORD=<TENANT2_SECRET_KEY>
|
||||
minio --config-dir ~/tenant2 server --address :9002 http://192.168.10.11/data/tenant2 http://192.168.10.12/data/tenant2 http://192.168.10.13/data/tenant2 http://192.168.10.14/data/tenant2
|
||||
|
||||
export MINIO_ACCESS_KEY=<TENANT3_ACCESS_KEY>
|
||||
export MINIO_SECRET_KEY=<TENANT3_SECRET_KEY>
|
||||
export MINIO_ROOT_USER=<TENANT3_ACCESS_KEY>
|
||||
export MINIO_ROOT_PASSWORD=<TENANT3_SECRET_KEY>
|
||||
minio --config-dir ~/tenant3 server --address :9003 http://192.168.10.11/data/tenant3 http://192.168.10.12/data/tenant3 http://192.168.10.13/data/tenant3 http://192.168.10.14/data/tenant3
|
||||
```
|
||||
|
||||
|
||||
@@ -121,9 +121,9 @@ spec:
|
||||
- /data
|
||||
env:
|
||||
# MinIO access key and secret key
|
||||
- name: MINIO_ACCESS_KEY
|
||||
- name: MINIO_ROOT_USER
|
||||
value: "minio"
|
||||
- name: MINIO_SECRET_KEY
|
||||
- name: MINIO_ROOT_PASSWORD
|
||||
value: "minio123"
|
||||
ports:
|
||||
- containerPort: 9000
|
||||
@@ -273,9 +273,9 @@ spec:
|
||||
containers:
|
||||
- name: minio
|
||||
env:
|
||||
- name: MINIO_ACCESS_KEY
|
||||
- name: MINIO_ROOT_USER
|
||||
value: "minio"
|
||||
- name: MINIO_SECRET_KEY
|
||||
- name: MINIO_ROOT_PASSWORD
|
||||
value: "minio123"
|
||||
image: minio/minio:RELEASE.2017-05-05T01-14-51Z
|
||||
args:
|
||||
@@ -459,9 +459,9 @@ spec:
|
||||
- gcp_project_id
|
||||
env:
|
||||
# MinIO access key and secret key
|
||||
- name: MINIO_ACCESS_KEY
|
||||
- name: MINIO_ROOT_USER
|
||||
value: "minio"
|
||||
- name: MINIO_SECRET_KEY
|
||||
- name: MINIO_ROOT_PASSWORD
|
||||
value: "minio123"
|
||||
# Google Cloud Service uses this variable
|
||||
- name: GOOGLE_APPLICATION_CREDENTIALS
|
||||
|
||||
@@ -33,8 +33,8 @@ MinIO共享模式是为了解决在真实场景中存在的一些问题,而且
|
||||
你需要将文件夹指向共享存储,比如`/path/to/nfs-volume`,然后在所有MinIO节点上运行下面的命令。
|
||||
|
||||
```sh
|
||||
export MINIO_ACCESS_KEY=<ACCESS_KEY>
|
||||
export MINIO_SECRET_KEY=<SECRET_KEY>
|
||||
export MINIO_ROOT_USER=<ACCESS_KEY>
|
||||
export MINIO_ROOT_PASSWORD=<SECRET_KEY>
|
||||
minio gateway nas /path/to/nfs-volume
|
||||
```
|
||||
|
||||
@@ -43,8 +43,8 @@ minio gateway nas /path/to/nfs-volume
|
||||
你需要将文件夹指向共享存储,比如`\\remote-server\smb`. 然后在所有MinIO节点上运行下面的命令。
|
||||
|
||||
```cmd
|
||||
set MINIO_ACCESS_KEY=my-username
|
||||
set MINIO_SECRET_KEY=my-password
|
||||
set MINIO_ROOT_USER=my-username
|
||||
set MINIO_ROOT_PASSWORD=my-password
|
||||
minio.exe gateway nas \\remote-server\smb\export
|
||||
```
|
||||
|
||||
@@ -53,8 +53,8 @@ minio.exe gateway nas \\remote-server\smb\export
|
||||
如果一个远程的volume, 比如`\\remote-server\smb`挂载成一个硬盘, 比如`M:\`. 你可以使用[`net use`](https://technet.microsoft.com/en-us/library/bb490717.aspx)命令将这块盘映射到一个文件夹。
|
||||
|
||||
```cmd
|
||||
set MINIO_ACCESS_KEY=my-username
|
||||
set MINIO_SECRET_KEY=my-password
|
||||
set MINIO_ROOT_USER=my-username
|
||||
set MINIO_ROOT_PASSWORD=my-password
|
||||
net use m: \\remote-server\smb\export /P:Yes
|
||||
minio.exe gateway nas M:\export
|
||||
```
|
||||
|
||||
@@ -15,8 +15,8 @@ MinIO服务器允许限制传入的请求:
|
||||
|
||||
```sh
|
||||
export MINIO_API_REQUESTS_MAX=1600
|
||||
export MINIO_ACCESS_KEY=your-access-key
|
||||
export MINIO_SECRET_KEY=your-secret-key
|
||||
export MINIO_ROOT_USER=your-access-key
|
||||
export MINIO_ROOT_PASSWORD=your-secret-key
|
||||
minio server http://server{1...8}/mnt/hdd{1...16}
|
||||
```
|
||||
|
||||
@@ -39,8 +39,8 @@ mc admin service restart myminio/
|
||||
```sh
|
||||
export MINIO_API_REQUESTS_MAX=1600
|
||||
export MINIO_API_REQUESTS_DEADLINE=2m
|
||||
export MINIO_ACCESS_KEY=your-access-key
|
||||
export MINIO_SECRET_KEY=your-secret-key
|
||||
export MINIO_ROOT_USER=your-access-key
|
||||
export MINIO_ROOT_PASSWORD=your-secret-key
|
||||
minio server http://server{1...8}/mnt/hdd{1...16}
|
||||
```
|
||||
|
||||
|
||||
@@ -44,8 +44,8 @@ cat <<EOF >> $RPM_BUILD_ROOT/etc/default/minio
|
||||
|
||||
# Root credentials for the server.
|
||||
# Uncomment both lines before starting the server.
|
||||
# MINIO_ACCESS_KEY=Server-Access-Key
|
||||
# MINIO_SECRET_KEY=Server-Secret-Key
|
||||
# MINIO_ROOT_USER=Server-Root-User
|
||||
# MINIO_ROOT_PASSWORD=Server-Root-Password
|
||||
|
||||
MINIO_OPTS="--certs-dir /etc/minio/certs"
|
||||
EOF
|
||||
|
||||
Reference in New Issue
Block a user