mirror of
https://github.com/minio/minio.git
synced 2025-11-10 05:59:43 -05:00
feat: Deprecate embedded browser and import console (#12460)
This feature also changes the default port where the browser is running, now the port has moved to 9001 and it can be configured with ``` --console-address ":9001" ```
This commit is contained in:
@@ -308,7 +308,7 @@ Once set the healer settings are automatically applied without the need for serv
|
||||
|
||||
### Browser
|
||||
|
||||
Enable or disable access to web UI. By default it is set to `on`. You may override this field with `MINIO_BROWSER` environment variable.
|
||||
Enable or disable access to console web UI. By default it is set to `on`. You may override this field with `MINIO_BROWSER` environment variable.
|
||||
|
||||
Example:
|
||||
|
||||
|
||||
@@ -5,4 +5,3 @@ MinIO Gateway adds Amazon S3 compatibility to third party cloud storage provider
|
||||
- [HDFS](https://github.com/minio/minio/blob/master/docs/gateway/hdfs.md)
|
||||
- [S3](https://github.com/minio/minio/blob/master/docs/gateway/s3.md)
|
||||
- [Google Cloud Storage](https://github.com/minio/minio/blob/master/docs/gateway/gcs.md)
|
||||
|
||||
|
||||
@@ -16,10 +16,13 @@ export MINIO_ROOT_USER=azureaccountname
|
||||
export MINIO_ROOT_PASSWORD=azureaccountkey
|
||||
minio gateway azure
|
||||
```
|
||||
## Test using MinIO Browser
|
||||
## Test using MinIO Console
|
||||
MinIO Gateway comes with an embedded web based object browser. Point your web browser to http://127.0.0.1:9000 to ensure that your server has started successfully.
|
||||
|
||||

|
||||
| Dashboard | Creating a bucket |
|
||||
| ------------- | ------------- |
|
||||
| 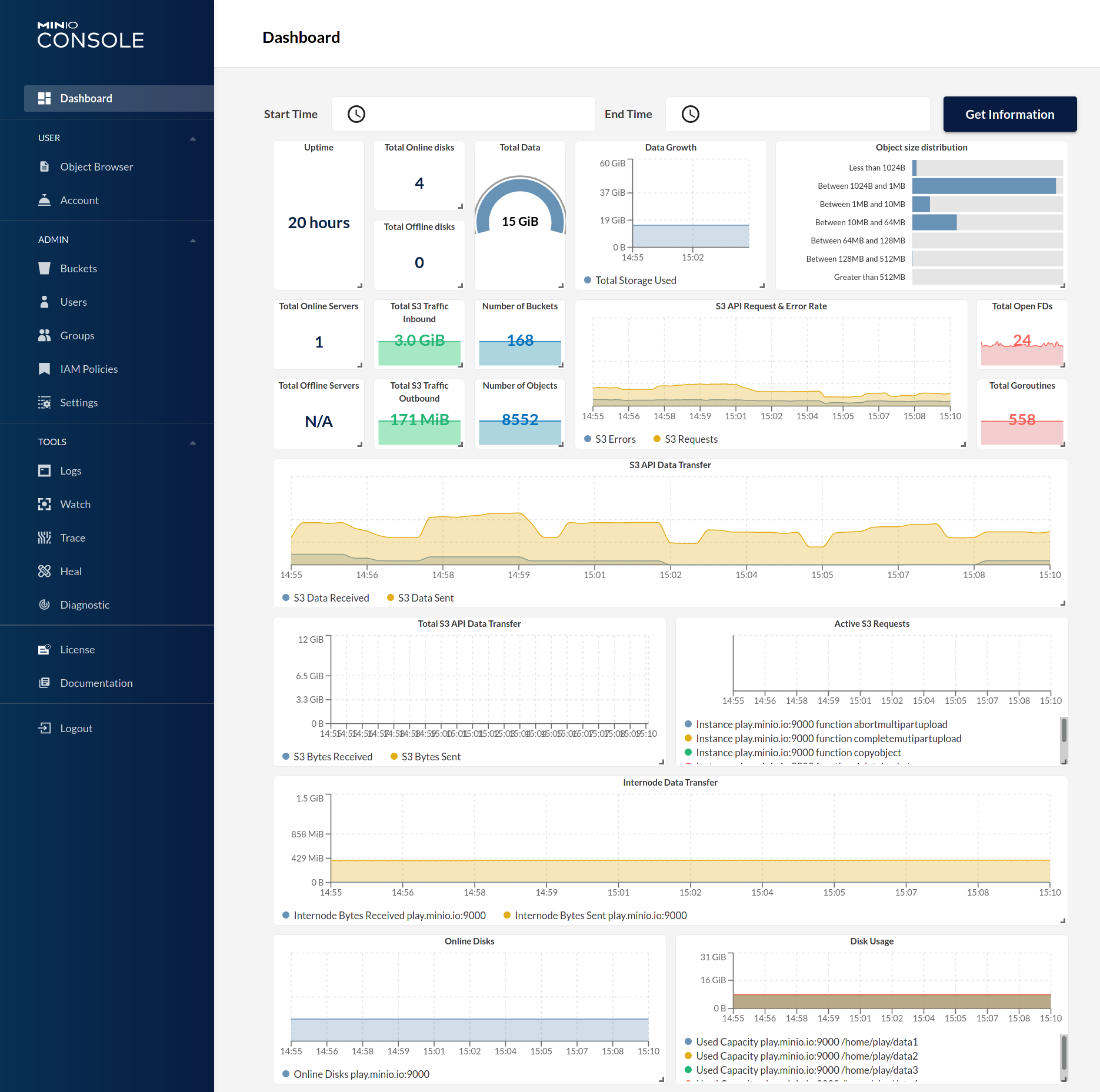 | 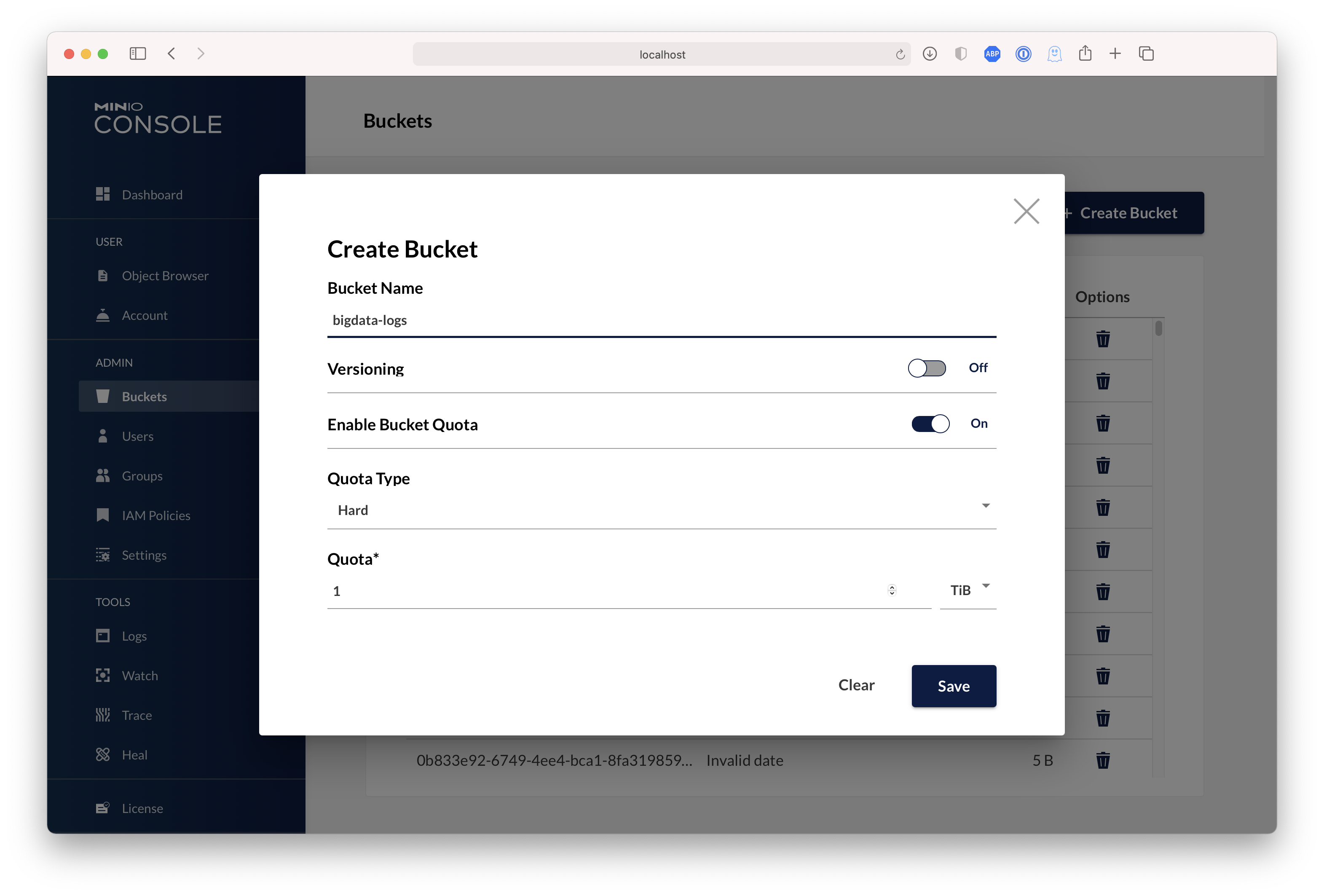 |
|
||||
|
||||
## Test using MinIO Client `mc`
|
||||
`mc` provides a modern alternative to UNIX commands such as ls, cat, cp, mirror, diff etc. It supports filesystems and Amazon S3 compatible cloud storage services.
|
||||
|
||||
|
||||
@@ -3,10 +3,10 @@
|
||||
MinIO GCS Gateway allows you to access Google Cloud Storage (GCS) with Amazon S3-compatible APIs
|
||||
|
||||
- [Run MinIO Gateway for GCS](#run-minio-gateway-for-gcs)
|
||||
- [Test Using MinIO Browser](#test-using-minio-browser)
|
||||
- [Test Using MinIO Console](#test-using-minio-browser)
|
||||
- [Test Using MinIO Client](#test-using-minio-client)
|
||||
|
||||
## <a name="run-minio-gateway-for-gcs"></a>1. Run MinIO Gateway for GCS
|
||||
## 1. Run MinIO Gateway for GCS
|
||||
|
||||
### 1.1 Create a Service Account key for GCS and get the Credentials File
|
||||
1. Navigate to the [API Console Credentials page](https://console.developers.google.com/project/_/apis/credentials).
|
||||
@@ -38,13 +38,15 @@ export MINIO_ROOT_PASSWORD=miniosecretkey
|
||||
minio gateway gcs yourprojectid
|
||||
```
|
||||
|
||||
## <a name="test-using-minio-browser"></a>2. Test Using MinIO Browser
|
||||
## 2. Test Using MinIO Console
|
||||
|
||||
MinIO Gateway comes with an embedded web-based object browser that outputs content to http://127.0.0.1:9000. To test that MinIO Gateway is running, open a web browser, navigate to http://127.0.0.1:9000, and ensure that the object browser is displayed.
|
||||
|
||||

|
||||
| Dashboard | Creating a bucket |
|
||||
| ------------- | ------------- |
|
||||
|  |  |
|
||||
|
||||
## <a name="test-using-minio-client"></a>3. Test Using MinIO Client
|
||||
## 3. Test Using MinIO Client
|
||||
|
||||
MinIO Client is a command-line tool called `mc` that provides UNIX-like commands for interacting with the server (e.g. ls, cat, cp, mirror, diff, find, etc.). `mc` supports file systems and Amazon S3-compatible cloud storage services (AWS Signature v2 and v4).
|
||||
|
||||
@@ -82,7 +84,7 @@ Other limitations:
|
||||
|
||||
* Bucket notification APIs are not supported.
|
||||
|
||||
## <a name="explore-further"></a>4. Explore Further
|
||||
## 4. Explore Further
|
||||
- [`mc` command-line interface](https://docs.min.io/docs/minio-client-quickstart-guide)
|
||||
- [`aws` command-line interface](https://docs.min.io/docs/aws-cli-with-minio)
|
||||
- [`minio-go` Go SDK](https://docs.min.io/docs/golang-client-quickstart-guide)
|
||||
|
||||
@@ -68,10 +68,12 @@ export KRB5USERNAME=hdfs
|
||||
export KRB5REALM=REALM.COM
|
||||
```
|
||||
|
||||
## Test using MinIO Browser
|
||||
## Test using MinIO Console
|
||||
*MinIO gateway* comes with an embedded web based object browser. Point your web browser to http://127.0.0.1:9000 to ensure that your server has started successfully.
|
||||
|
||||

|
||||
| Dashboard | Creating a bucket |
|
||||
| ------------- | ------------- |
|
||||
|  |  |
|
||||
|
||||
## Test using MinIO Client `mc`
|
||||
|
||||
|
||||
@@ -24,11 +24,13 @@ export MINIO_ROOT_PASSWORD=minio123
|
||||
minio gateway nas /shared/nasvol
|
||||
```
|
||||
|
||||
## Test using MinIO Browser
|
||||
## Test using MinIO Console
|
||||
|
||||
MinIO Gateway comes with an embedded web based object browser. Point your web browser to http://127.0.0.1:9000 to ensure that your server has started successfully.
|
||||
|
||||

|
||||
| Dashboard | Creating a bucket |
|
||||
| ------------- | ------------- |
|
||||
|  |  |
|
||||
|
||||
## Test using MinIO Client `mc`
|
||||
|
||||
|
||||
@@ -1,6 +1,6 @@
|
||||
# MinIO S3 Gateway [](https://slack.min.io)
|
||||
|
||||
MinIO S3 Gateway adds MinIO features like MinIO Browser and disk caching to AWS S3 or any other AWS S3 compatible service.
|
||||
MinIO S3 Gateway adds MinIO features like MinIO Console and disk caching to AWS S3 or any other AWS S3 compatible service.
|
||||
|
||||
## Run MinIO Gateway for AWS S3
|
||||
As a prerequisite to run MinIO S3 gateway, you need valid AWS S3 access key and secret key by default. Optionally you can also set custom access/secret key, when you have rotating AWS IAM credentials or AWS credentials through environment variables (i.e. AWS_ACCESS_KEY_ID)
|
||||
@@ -115,12 +115,14 @@ MinIO edge caching allows storing content closer to the applications. Frequently
|
||||
|
||||
Refer [this document](https://docs.min.io/docs/minio-disk-cache-guide.html) to get started with MinIO Caching.
|
||||
|
||||
## MinIO Browser
|
||||
## MinIO Console
|
||||
MinIO Gateway comes with an embedded web based object browser. Point your web browser to http://127.0.0.1:9000 to ensure that your server has started successfully.
|
||||
|
||||

|
||||
| Dashboard | Creating a bucket |
|
||||
| ------------- | ------------- |
|
||||
|  |  |
|
||||
|
||||
With MinIO S3 gateway, you can use MinIO browser to explore AWS S3 based objects.
|
||||
With MinIO S3 gateway, you can use MinIO Console to explore AWS S3 based objects.
|
||||
|
||||
### Known limitations
|
||||
|
||||
|
||||
Binary file not shown.
|
Before Width: | Height: | Size: 111 KiB |
Binary file not shown.
|
Before Width: | Height: | Size: 106 KiB |
BIN
docs/screenshots/pic1.png
Normal file
BIN
docs/screenshots/pic1.png
Normal file
Binary file not shown.
|
After Width: | Height: | Size: 314 KiB |
BIN
docs/screenshots/pic2.png
Normal file
BIN
docs/screenshots/pic2.png
Normal file
Binary file not shown.
|
After Width: | Height: | Size: 1.6 MiB |
@@ -92,11 +92,10 @@ This will open the login page of keycloak, upon successful login, STS credential
|
||||
|
||||
These credentials can now be used to perform MinIO API operations.
|
||||
|
||||
### Using MinIO Browser
|
||||
### Using MinIO Console
|
||||
|
||||
- Open MinIO URL on the browser, lets say http://localhost:9000
|
||||
- Click on `Log in with OpenID`
|
||||
- Provide `Client ID` and press ENTER, if `client_id` is already configured for MinIO this page will automatically redirect to Keycloak user login page.
|
||||
- Open MinIO URL on the browser, lets say http://localhost:9000/
|
||||
- Click on `Login with SSO`
|
||||
- User will be redirected to the Keycloak user login page, upon successful login the user will be redirected to MinIO page and logged in automatically,
|
||||
the user should see now the buckets and objects they have access to.
|
||||
|
||||
|
||||
@@ -1,22 +1,5 @@
|
||||
# AssumeRole [](https://slack.min.io)
|
||||
|
||||
**Table of Contents**
|
||||
|
||||
- [Introduction](#introduction)
|
||||
- [API Request Parameters](#api-request-parameters)
|
||||
- [Version](#version)
|
||||
- [AUTHPARAMS](#authparams)
|
||||
- [DurationSeconds](#durationseconds)
|
||||
- [Policy](#policy)
|
||||
- [Response Elements](#response-elements)
|
||||
- [Errors](#errors)
|
||||
- [Sample `POST` Request](#sample-post-request)
|
||||
- [Sample Response](#sample-response)
|
||||
- [Using AssumeRole API](#using-assumerole-api)
|
||||
- [Explore Further](#explore-further)
|
||||
|
||||
<!-- markdown-toc end -->
|
||||
|
||||
## Introduction
|
||||
|
||||
Returns a set of temporary security credentials that you can use to access MinIO resources. AssumeRole requires authorization credentials for an existing user on MinIO. The advantages of this API are
|
||||
|
||||
@@ -1,20 +1,5 @@
|
||||
# AssumeRoleWithClientGrants [](https://slack.min.io)
|
||||
|
||||
**Table of Contents**
|
||||
|
||||
- [Introduction](#introduction)
|
||||
- [API Request Parameters](#api-request-parameters)
|
||||
- [Token](#token)
|
||||
- [Version](#version)
|
||||
- [DurationSeconds](#durationseconds)
|
||||
- [Policy](#policy)
|
||||
- [Response Elements](#response-elements)
|
||||
- [Errors](#errors)
|
||||
- [Sample `POST` Request](#sample-post-request)
|
||||
- [Sample Response](#sample-response)
|
||||
- [Using ClientGrants API](#using-clientgrants-api)
|
||||
- [Explore Further](#explore-further)
|
||||
|
||||
## Introduction
|
||||
|
||||
Returns a set of temporary security credentials for applications/clients who have been authenticated through client credential grants provided by identity provider. Example providers include KeyCloak, Okta etc.
|
||||
|
||||
@@ -114,11 +114,10 @@ This will open the login page of keycloak, upon successful login, STS credential
|
||||
|
||||
These credentials can now be used to perform MinIO API operations.
|
||||
|
||||
### Using MinIO Browser
|
||||
### Using MinIO Console
|
||||
|
||||
- Open MinIO URL on the browser, lets say http://localhost:9000
|
||||
- Click on `Log in with OpenID`
|
||||
- Provide `Client ID` and press ENTER, if `client_id` is already configured for MinIO this page will automatically redirect to Keycloak user login page.
|
||||
- Open MinIO URL on the browser, lets say http://localhost:9000/
|
||||
- Click on `Login with SSO`
|
||||
- User will be redirected to the Keycloak user login page, upon successful login the user will be redirected to MinIO page and logged in automatically,
|
||||
the user should see now the buckets and objects they have access to.
|
||||
|
||||
|
||||
@@ -1,29 +1,5 @@
|
||||
# AssumeRoleWithLDAPIdentity [](https://slack.min.io)
|
||||
|
||||
**Table of Contents**
|
||||
|
||||
- [AssumeRoleWithLDAPIdentity [](https://slack.min.io)](#assumerolewithldapidentity-slackhttpsslackminioslacktypesvghttpsslackminio)
|
||||
- [Introduction](#introduction)
|
||||
- [Configuring AD/LDAP on MinIO](#configuring-adldap-on-minio)
|
||||
- [Supported modes of operation](#supported-modes-of-operation)
|
||||
- [Lookup-Bind Mode](#lookup-bind-mode)
|
||||
- [Username-Format Mode](#username-format-mode)
|
||||
- [Group membership search](#group-membership-search)
|
||||
- [Variable substitution in AD/LDAP configuration strings](#variable-substitution-in-adldap-configuration-strings)
|
||||
- [Managing User/Group Access Policy](#managing-usergroup-access-policy)
|
||||
- [API Request Parameters](#api-request-parameters)
|
||||
- [LDAPUsername](#ldapusername)
|
||||
- [LDAPPassword](#ldappassword)
|
||||
- [Version](#version)
|
||||
- [Policy](#policy)
|
||||
- [Response Elements](#response-elements)
|
||||
- [Errors](#errors)
|
||||
- [Sample `POST` Request](#sample-post-request)
|
||||
- [Sample Response](#sample-response)
|
||||
- [Using LDAP STS API](#using-ldap-sts-api)
|
||||
- [Caveats](#caveats)
|
||||
- [Explore Further](#explore-further)
|
||||
|
||||
## Introduction
|
||||
|
||||
MinIO provides a custom STS API that allows integration with LDAP based corporate environments including Microsoft Active Directory. The MinIO server can be configured in two possible modes: either using a LDAP separate service account, called lookup-bind mode or in username-format mode. In either case the login flow for a user is the same as the STS flow:
|
||||
@@ -252,9 +228,6 @@ $ go run ldap.go -u foouser -p foopassword
|
||||
}
|
||||
```
|
||||
|
||||
## Caveats
|
||||
**LDAP STS credentials are not yet supported on MinIO Browser UI, we may add this feature in future releases.**
|
||||
|
||||
## Explore Further
|
||||
- [MinIO Admin Complete Guide](https://docs.min.io/docs/minio-admin-complete-guide.html)
|
||||
- [The MinIO documentation website](https://docs.min.io)
|
||||
|
||||
@@ -136,7 +136,7 @@ func main() {
|
||||
AuthURL: ddoc.AuthEndpoint,
|
||||
TokenURL: ddoc.TokenEndpoint,
|
||||
},
|
||||
RedirectURL: fmt.Sprintf("http://localhost:%d/oauth2/callback", port),
|
||||
RedirectURL: fmt.Sprintf("http://10.0.0.67:%d/oauth2/callback", port),
|
||||
Scopes: scopes,
|
||||
}
|
||||
|
||||
@@ -223,7 +223,7 @@ func main() {
|
||||
w.Write(c)
|
||||
})
|
||||
|
||||
address := fmt.Sprintf("localhost:%v", port)
|
||||
address := fmt.Sprintf(":%v", port)
|
||||
log.Printf("listening on http://%s/", address)
|
||||
log.Fatal(http.ListenAndServe(address, nil))
|
||||
}
|
||||
|
||||
@@ -1,22 +1,5 @@
|
||||
# AssumeRoleWithWebIdentity [](https://slack.min.io)
|
||||
|
||||
**Table of Contents**
|
||||
|
||||
- [Introduction](#introduction)
|
||||
- [API Request Parameters](#api-request-parameters)
|
||||
- [WebIdentityToken](#webidentitytoken)
|
||||
- [Version](#version)
|
||||
- [DurationSeconds](#durationseconds)
|
||||
- [Policy](#policy)
|
||||
- [Response Elements](#response-elements)
|
||||
- [Errors](#errors)
|
||||
- [Sample `POST` Request](#sample-post-request)
|
||||
- [Sample Response](#sample-response)
|
||||
- [Using WebIdentity API](#using-webidentity-api)
|
||||
- [Authorization Flow](#authorization-flow)
|
||||
- [Using MinIO Browser](#using-minio-browser)
|
||||
- [Explore Further](#explore-further)
|
||||
|
||||
## Introduction
|
||||
|
||||
Calling AssumeRoleWithWebIdentity does not require the use of MinIO default credentials. Therefore, you can distribute an application (for example, on mobile devices) that requests temporary security credentials without including MinIO default credentials in the application. Instead, the identity of the caller is validated by using a JWT access token from the web identity provider. The temporary security credentials returned by this API consists of an access key, a secret key, and a security token. Applications can use these temporary security credentials to sign calls to MinIO API operations.
|
||||
@@ -141,8 +124,8 @@ $ go run web-identity.go -cid 204367807228-ok7601k6gj1pgge7m09h7d79co8p35xx.apps
|
||||
- Once obtained the JWT id_token is further sent to STS endpoint i.e MinIO to retrive temporary credentials.
|
||||
- Temporary credentials are displayed on the browser upon successful retrieval.
|
||||
|
||||
## Using MinIO Browser
|
||||
To support WebIdentity login on MinIO Browser, set openid configuration and restart MinIO
|
||||
## Using MinIO Console
|
||||
To support WebIdentity based login for MinIO Console, set openid configuration and restart MinIO
|
||||
|
||||
```
|
||||
mc admin config set myminio identity_openid config_url="<CONFIG_URL>" client_id="<client_identifier>"
|
||||
@@ -158,10 +141,9 @@ Sample URLs for Keycloak are
|
||||
|
||||
JWT token returned by the Identity Provider should include a custom claim for the policy, this is required to create a STS user in MinIO. The name of the custom claim could be either `policy` or `<NAMESPACE_PREFIX>policy`. If there is no namespace then `claim_prefix` can be ingored. For example if the custom claim name is `https://min.io/policy` then, `claim_prefix` should be set as `https://min.io/`.
|
||||
|
||||
- Open MinIO Browser and click `Log in with OpenID`
|
||||
- Enter the `Client ID` obtained from Identity Provider and press ENTER, if not you can set a `client_id` on server to avoid this step.
|
||||
- Open MinIO Console and click `Login with SSO`
|
||||
- The user will be redirected to the Identity Provider login page
|
||||
- Upon successful login on Identity Provider page the user will be automatically logged into MinIO Browser
|
||||
- Upon successful login on Identity Provider page the user will be automatically logged into MinIO Console.
|
||||
|
||||
## Explore Further
|
||||
- [MinIO Admin Complete Guide](https://docs.min.io/docs/minio-admin-complete-guide.html)
|
||||
|
||||
Reference in New Issue
Block a user